(Link to) Heap Reference Materials
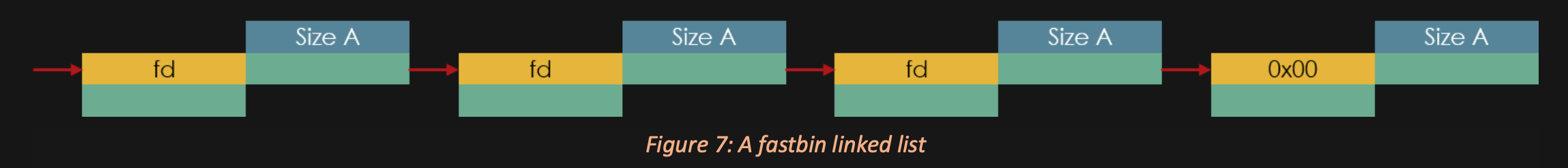
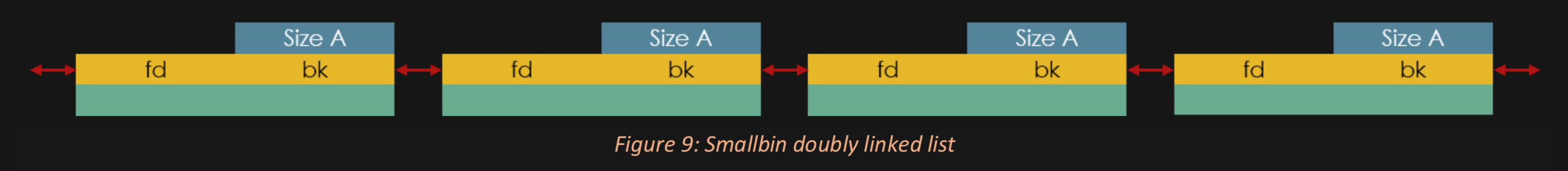
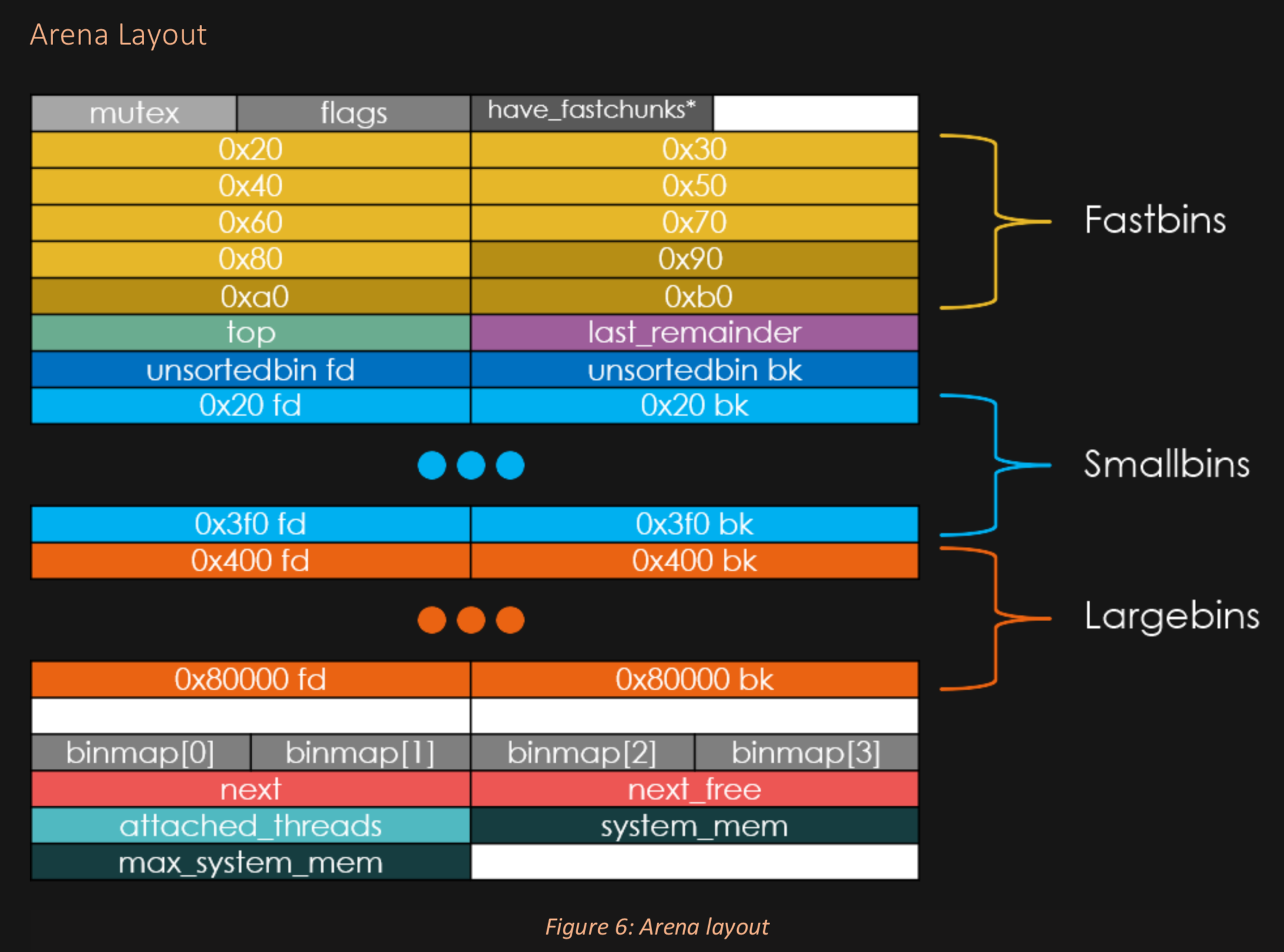
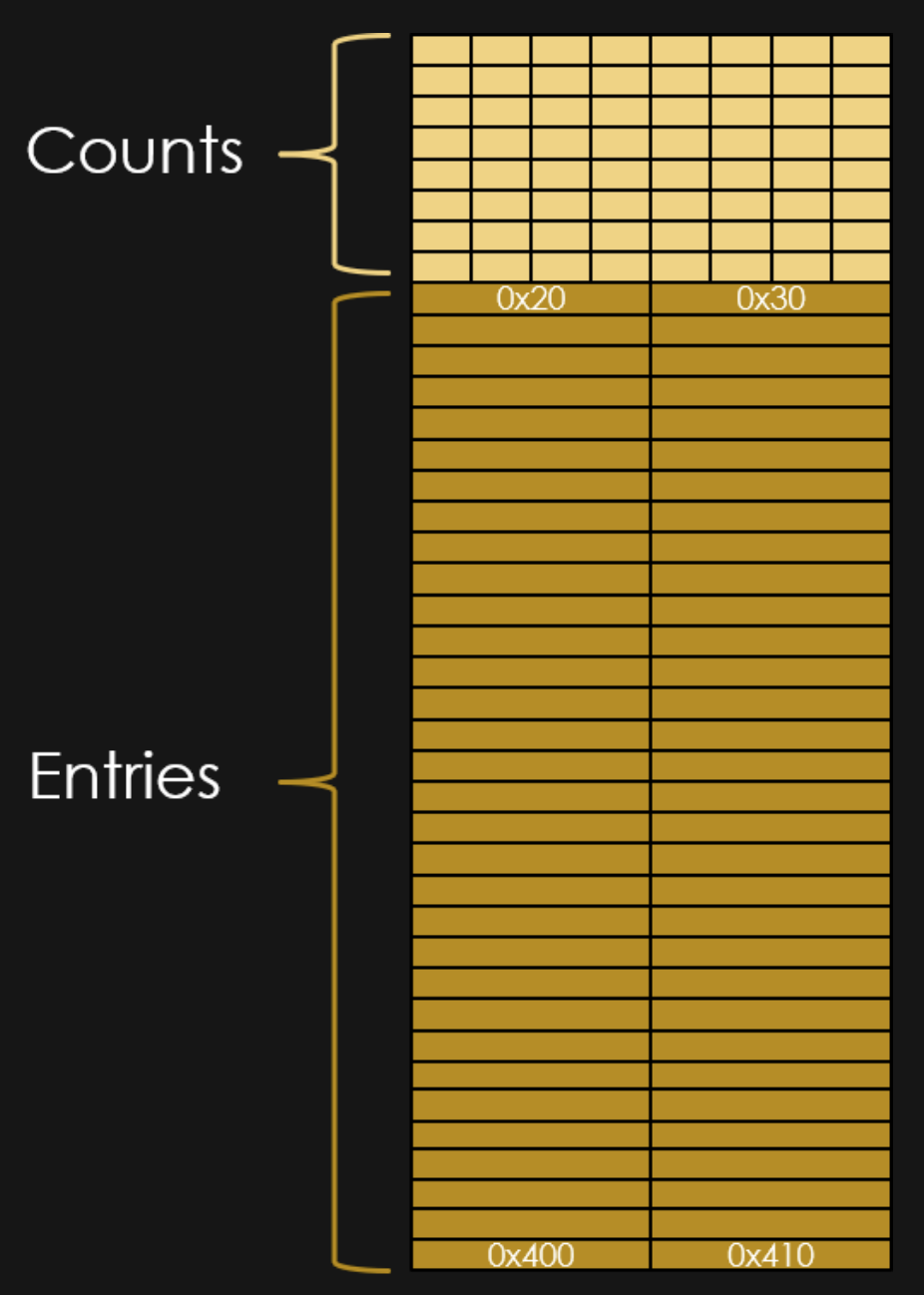
The Bins as Diagrams


Heap Flow Charts:
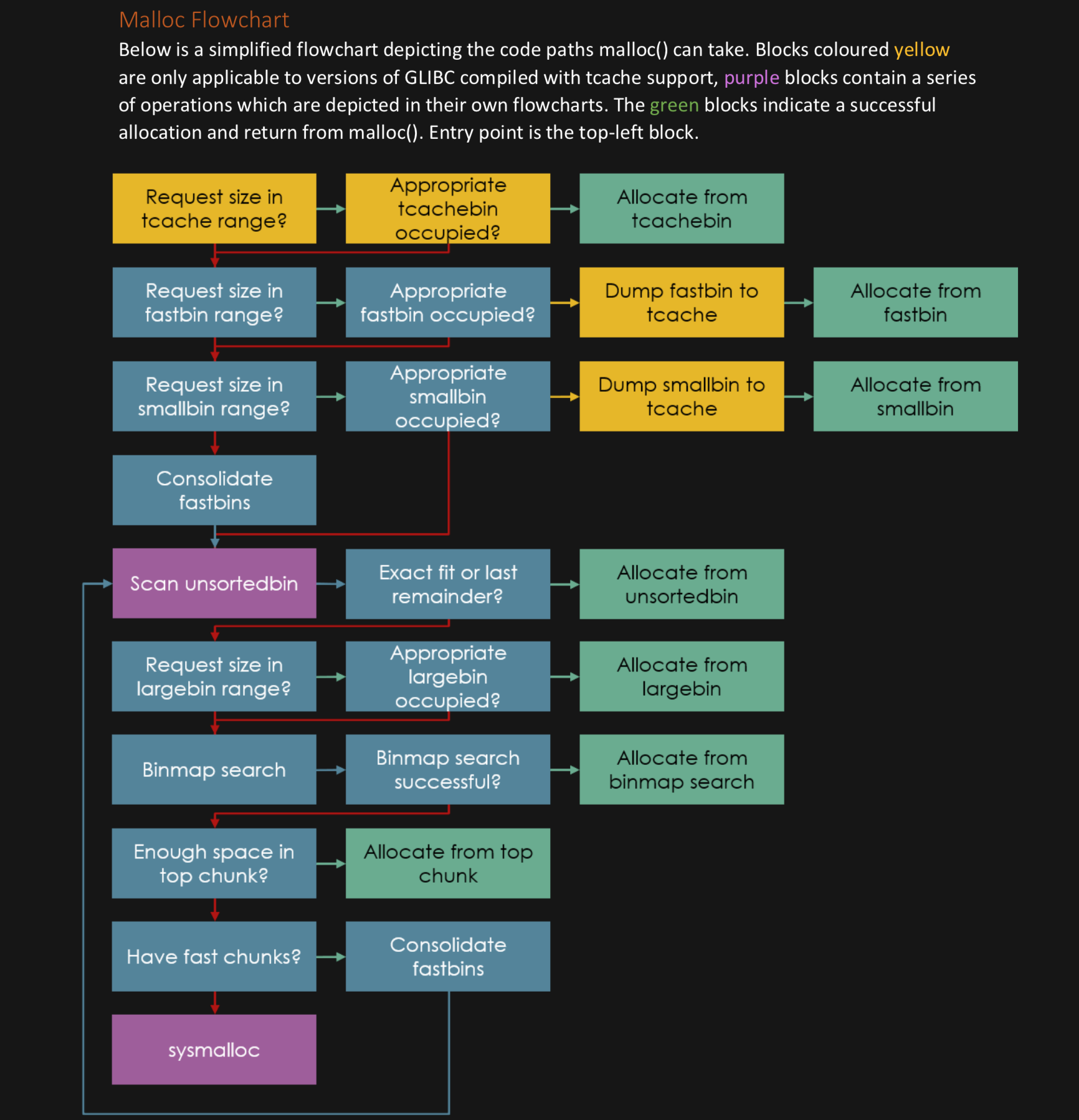
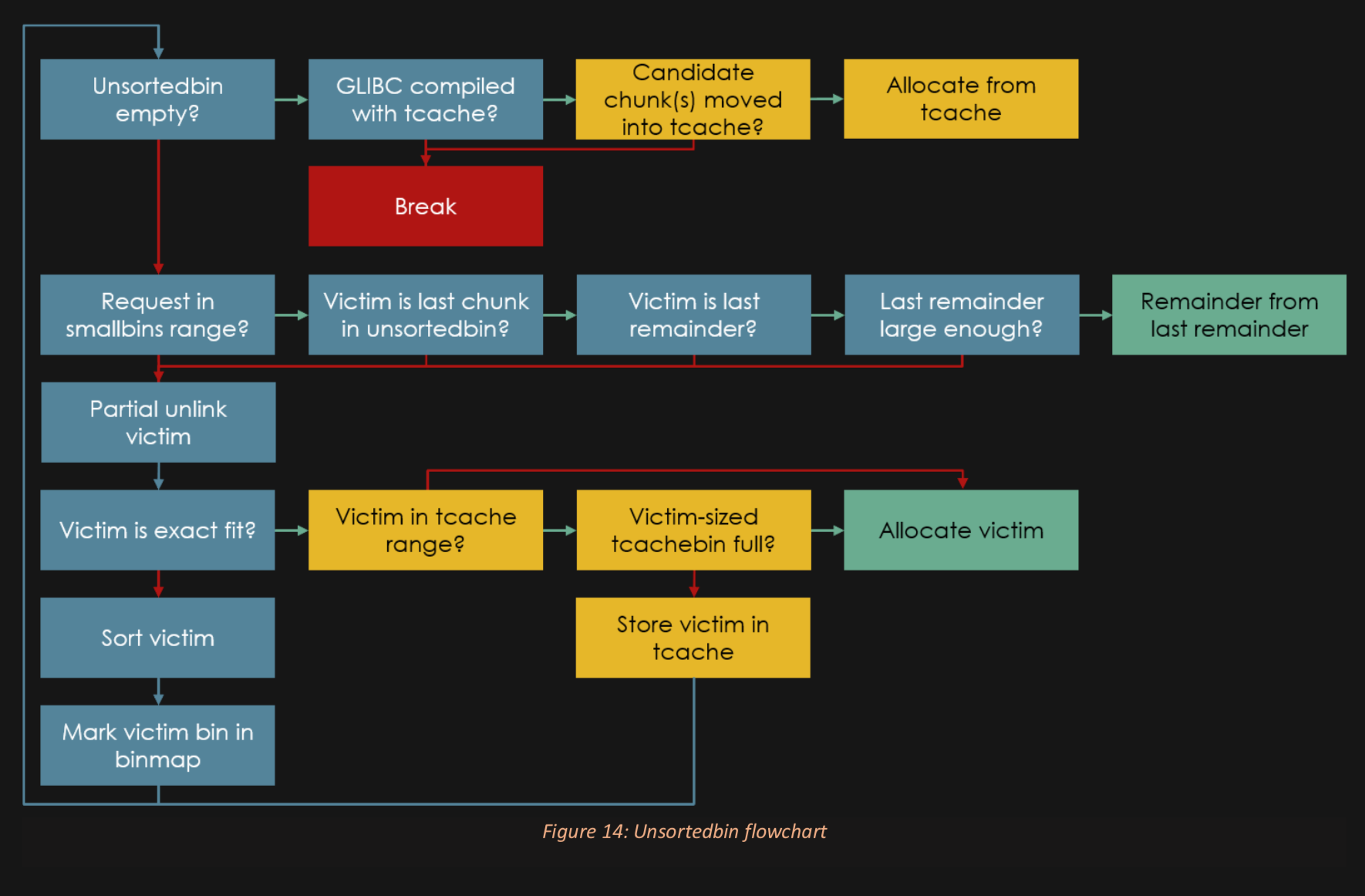
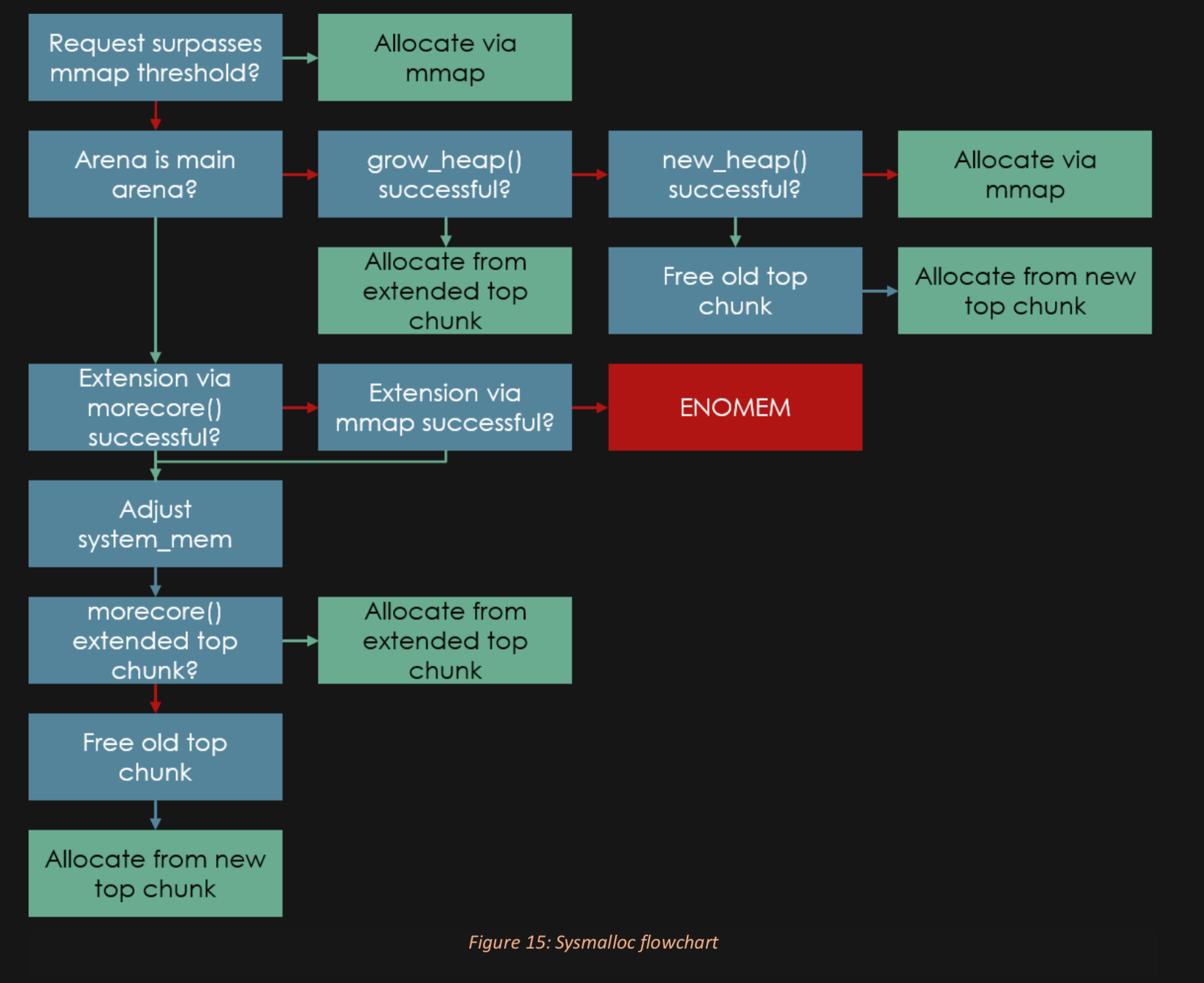
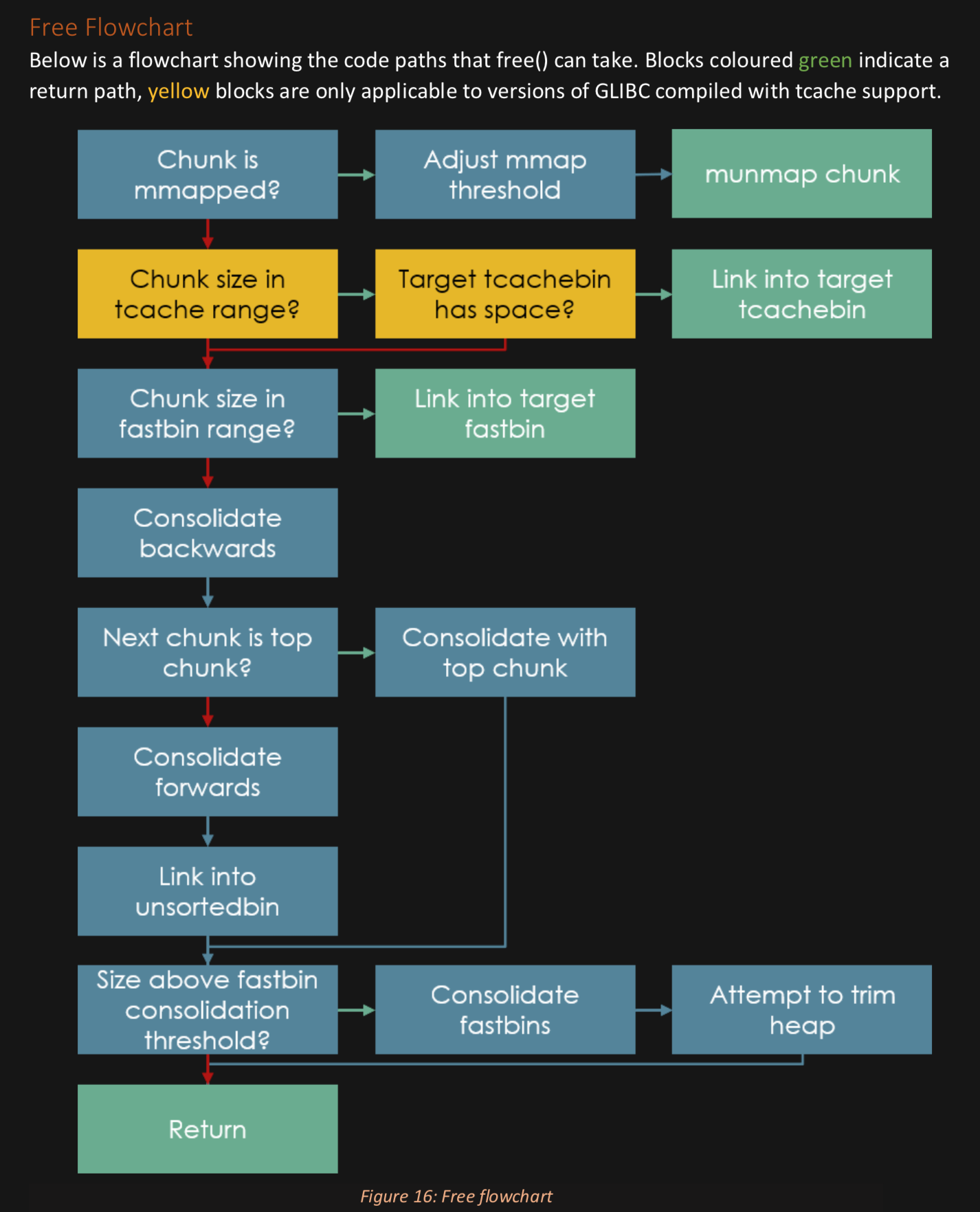
Don't like this style? Click here to change it! blue.css
Our compass through all of this is the desire for the following comfort food:
Challenges to the comfort of Mom's:
I have several expansions of heap exploitations planned.
Like, how to use an overflow to make some overlapping chunks. Or the beautiful exploit known as "poison null byte" (where all you can do is drop a 00 to a single overflow byte).
The situations you might face in a real-life PWN are manifold, and sometimes you get pure use-after-free but often the bug is much more subtle.
So I wanted to take a day and teach you how I learn new exploits. It does not have cool analogies yet, it has mysteries to unravel, it won't feel comfortable all the time. But every time you do one of these you unlock a new tool in your tool box.
You might want b *main, s for step, and heap chunks
Let's walk through the poison null byte demo at: https://github.com/shellphish/how2heap?tab=readme-ov-file#educational-heap-exploitation
Let's walk through the fast bin dup at: https://github.com/shellphish/how2heap?tab=readme-ov-file#educational-heap-exploitation
Let's walk through the unsafe unlink at: https://github.com/shellphish/how2heap?tab=readme-ov-file#educational-heap-exploitation









