(Link to) Heap Reference Materials
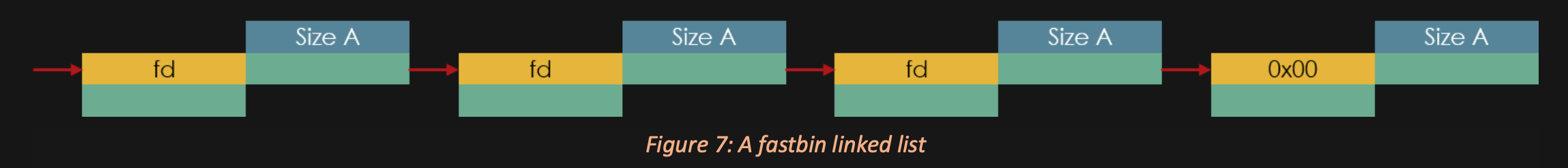
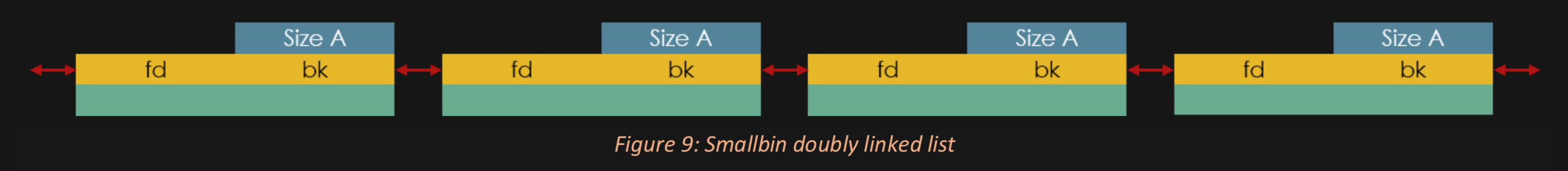
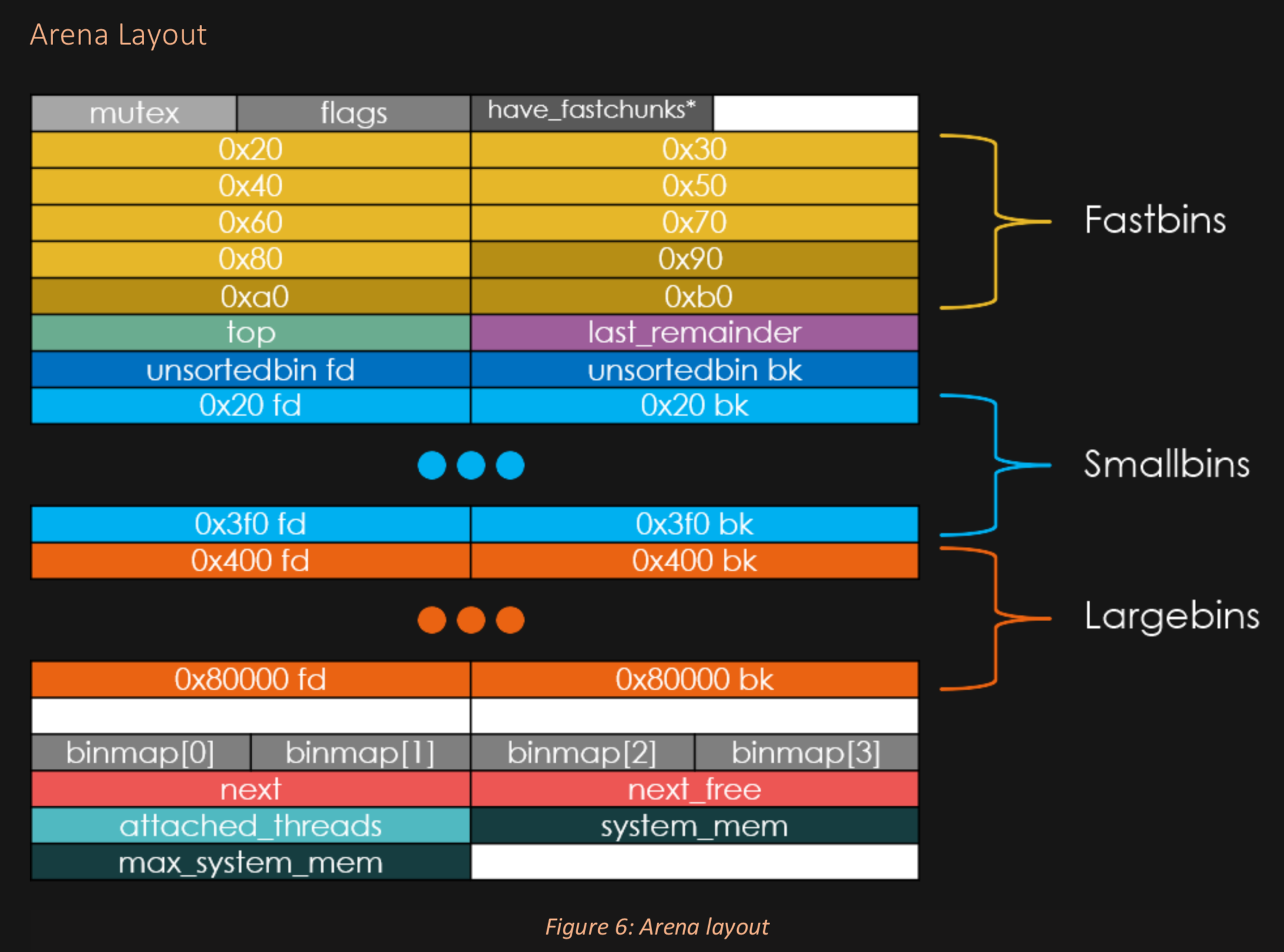
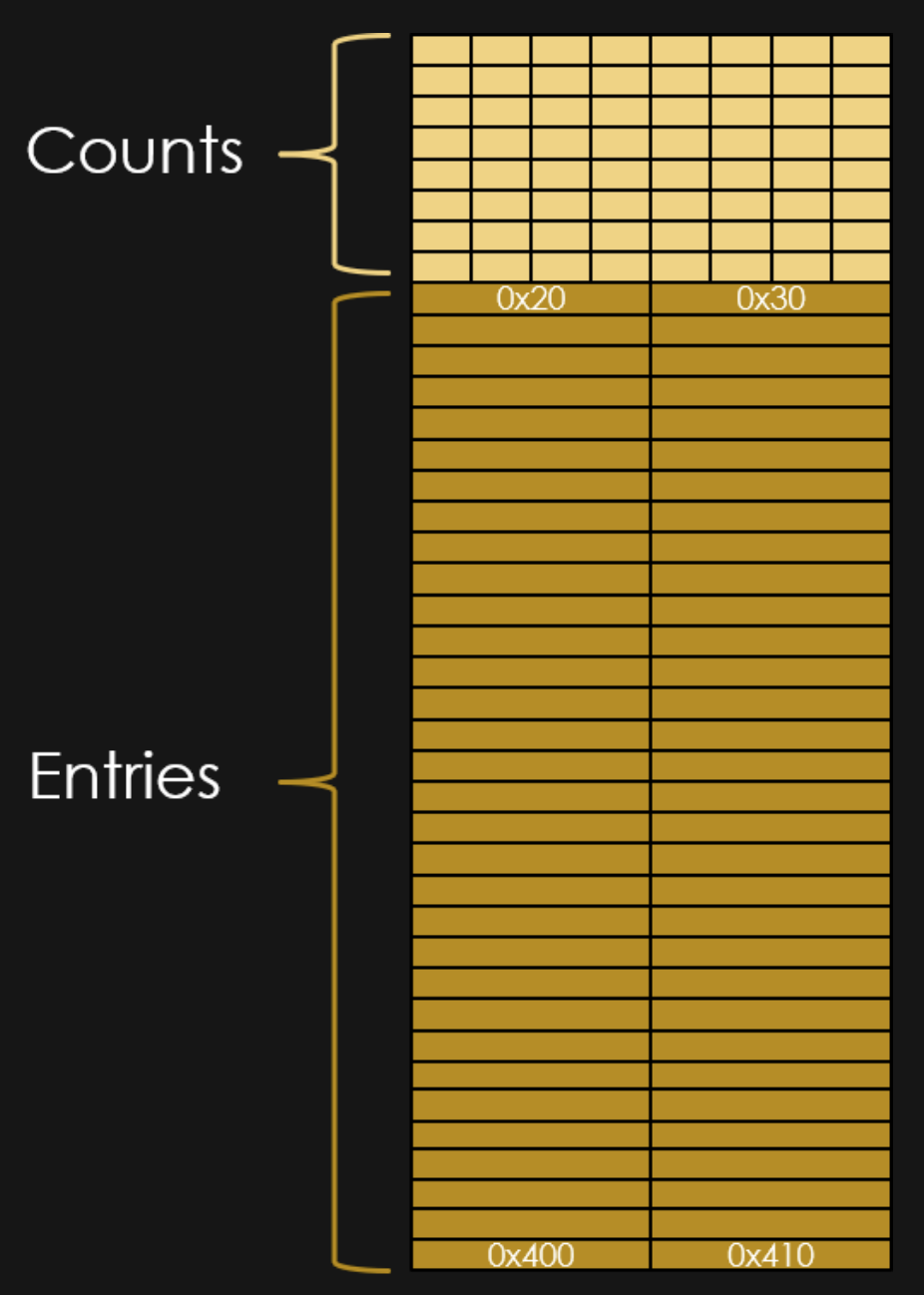
The Bins as Diagrams


Heap Flow Charts:
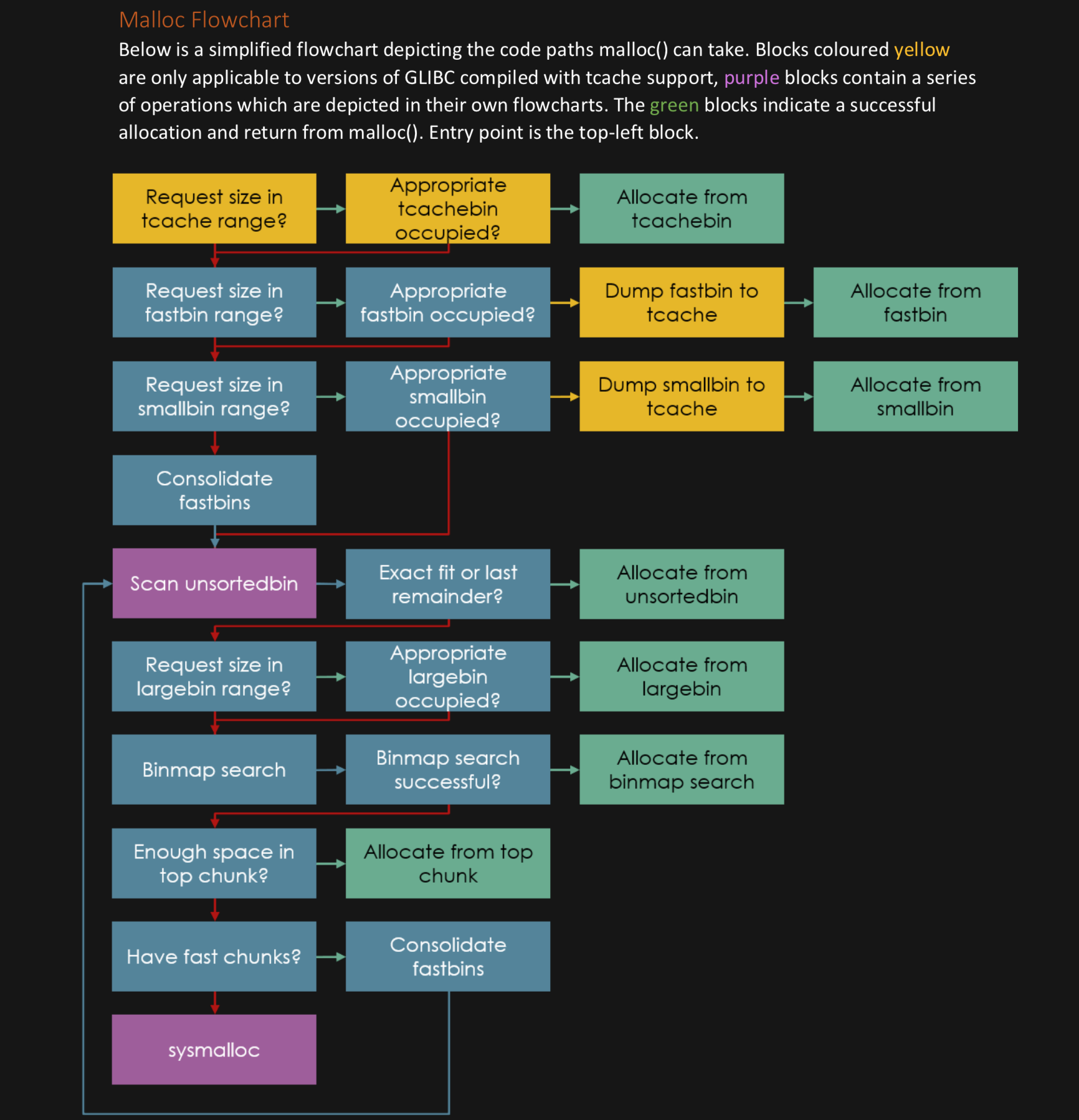
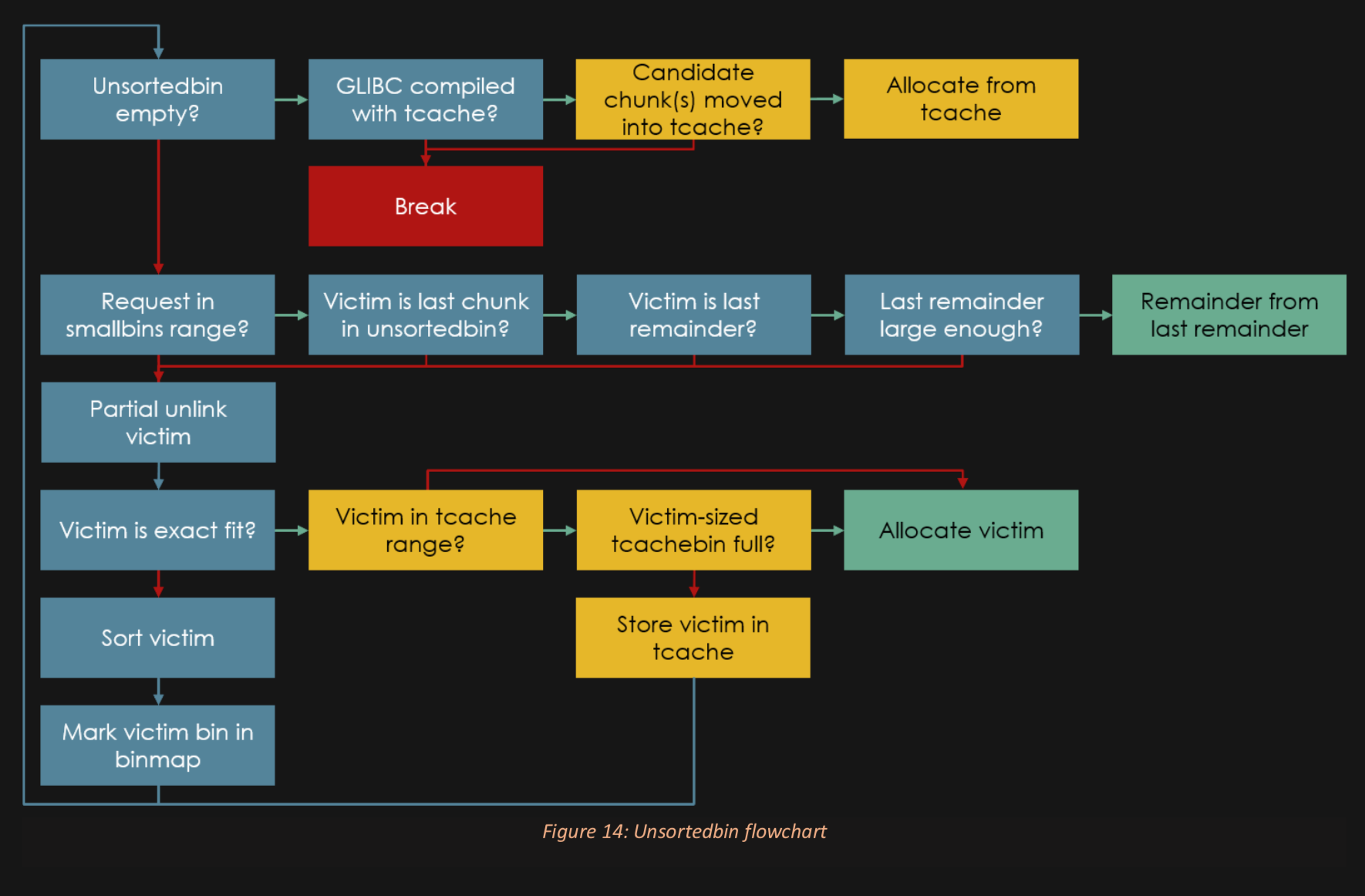
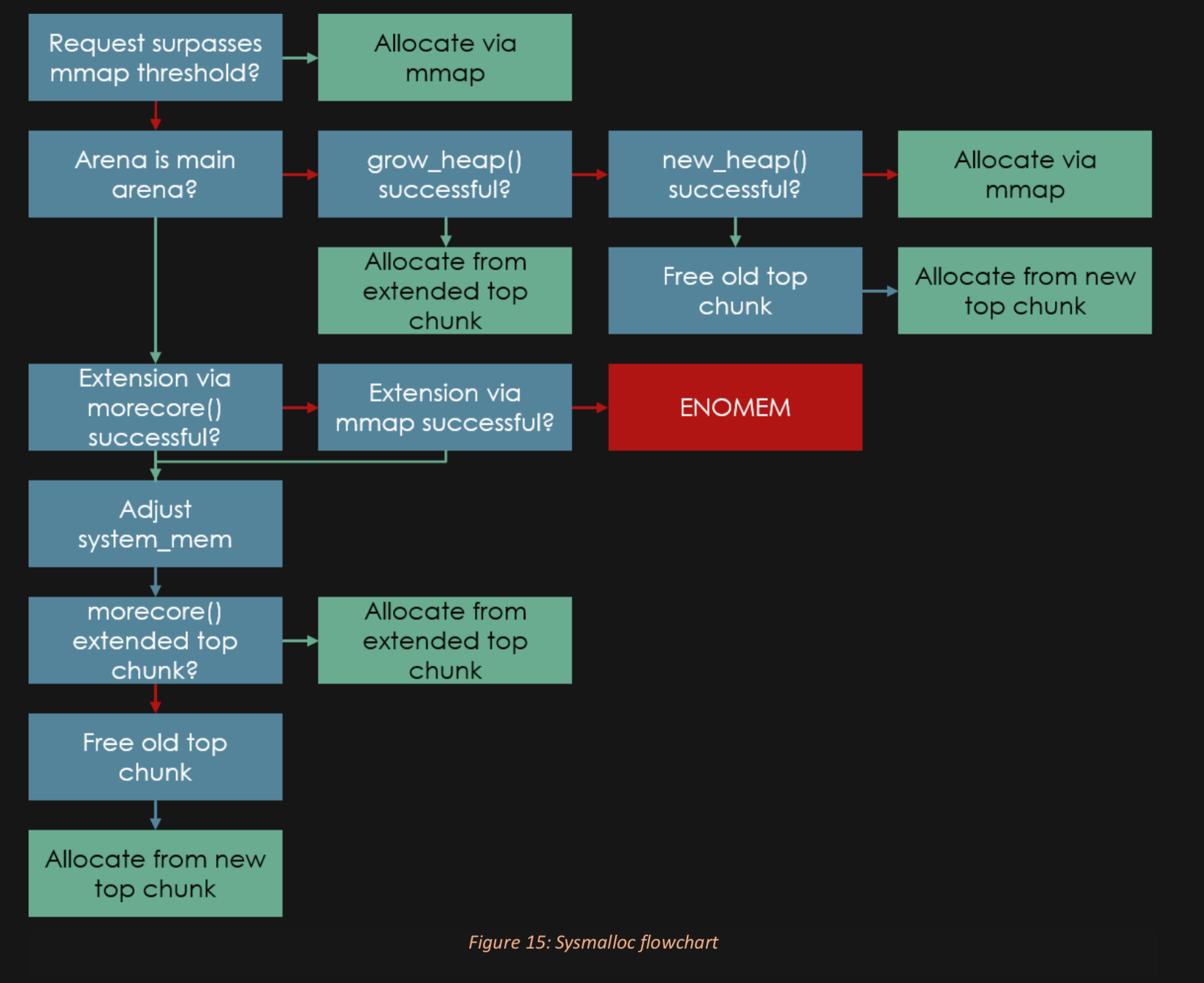
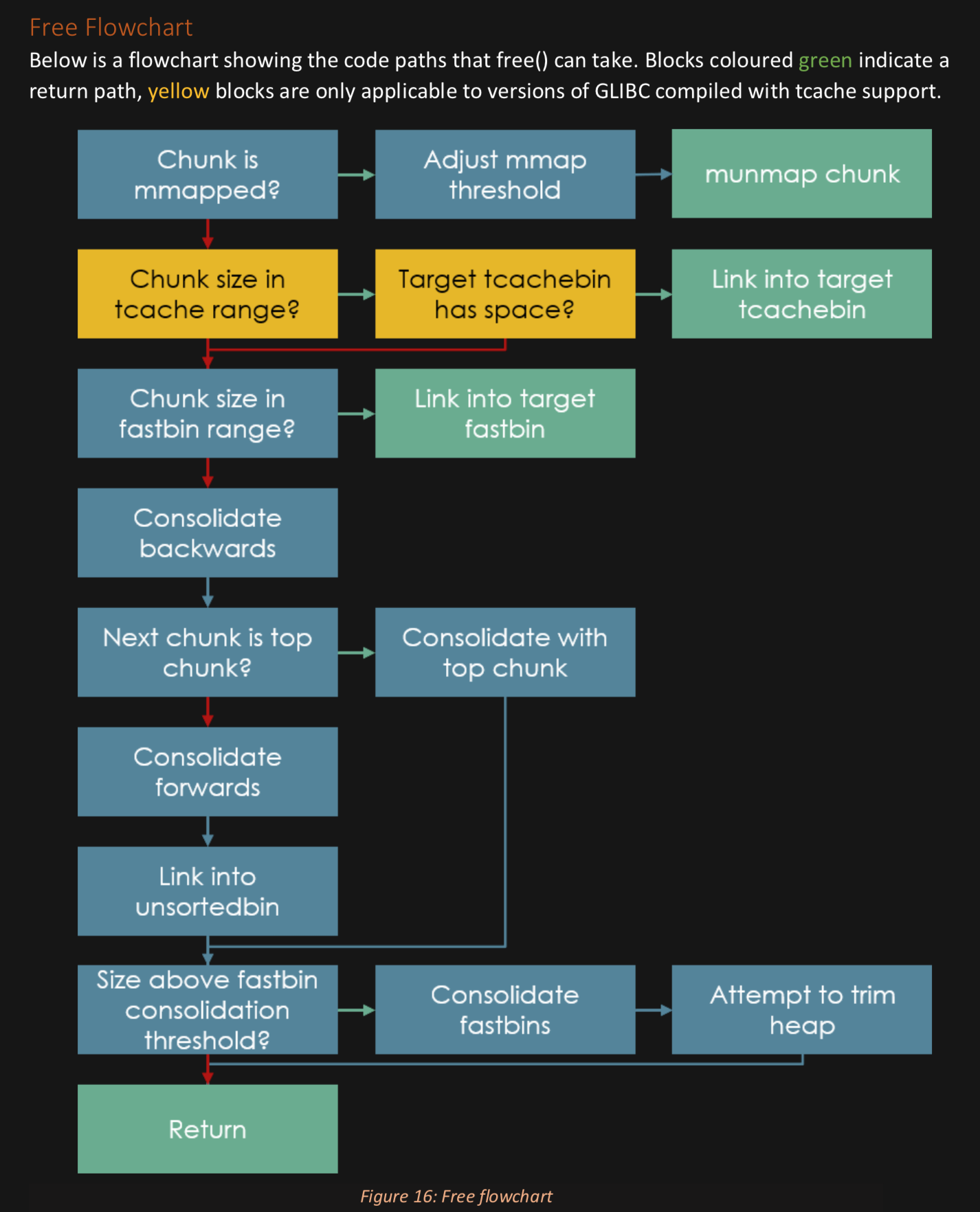
Don't like this style? Click here to change it! blue.css
Our compass through all of this is the desire for the following comfort food:
OK what if the developer wasn't as careless? They did NOT give us an arbitrary Use-After-Free? But they still made one mistake, which is the ability to "double-free" that is, I can free the same address twice... OK here is how we adapt MOM's for this new double-free situation.
So our goal is this:
This allows in-use memory to edit a free'd chunk in the tcache and now we resume mom's spaghetti.
I made a new zip for this: dubfree.zip









