(Link to) Heap Reference Materials
The Bins as Diagrams


Heap Flow Charts:
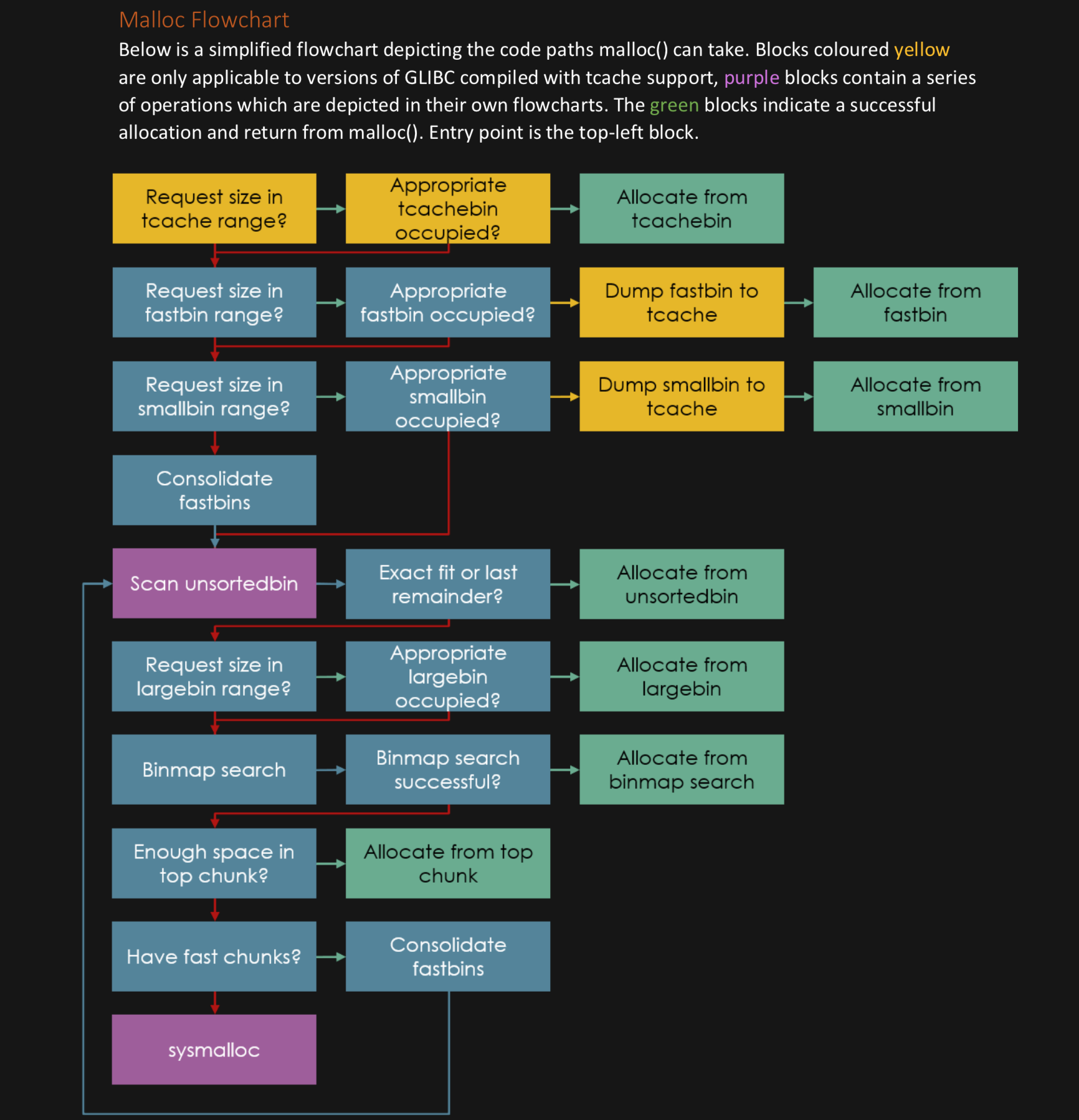
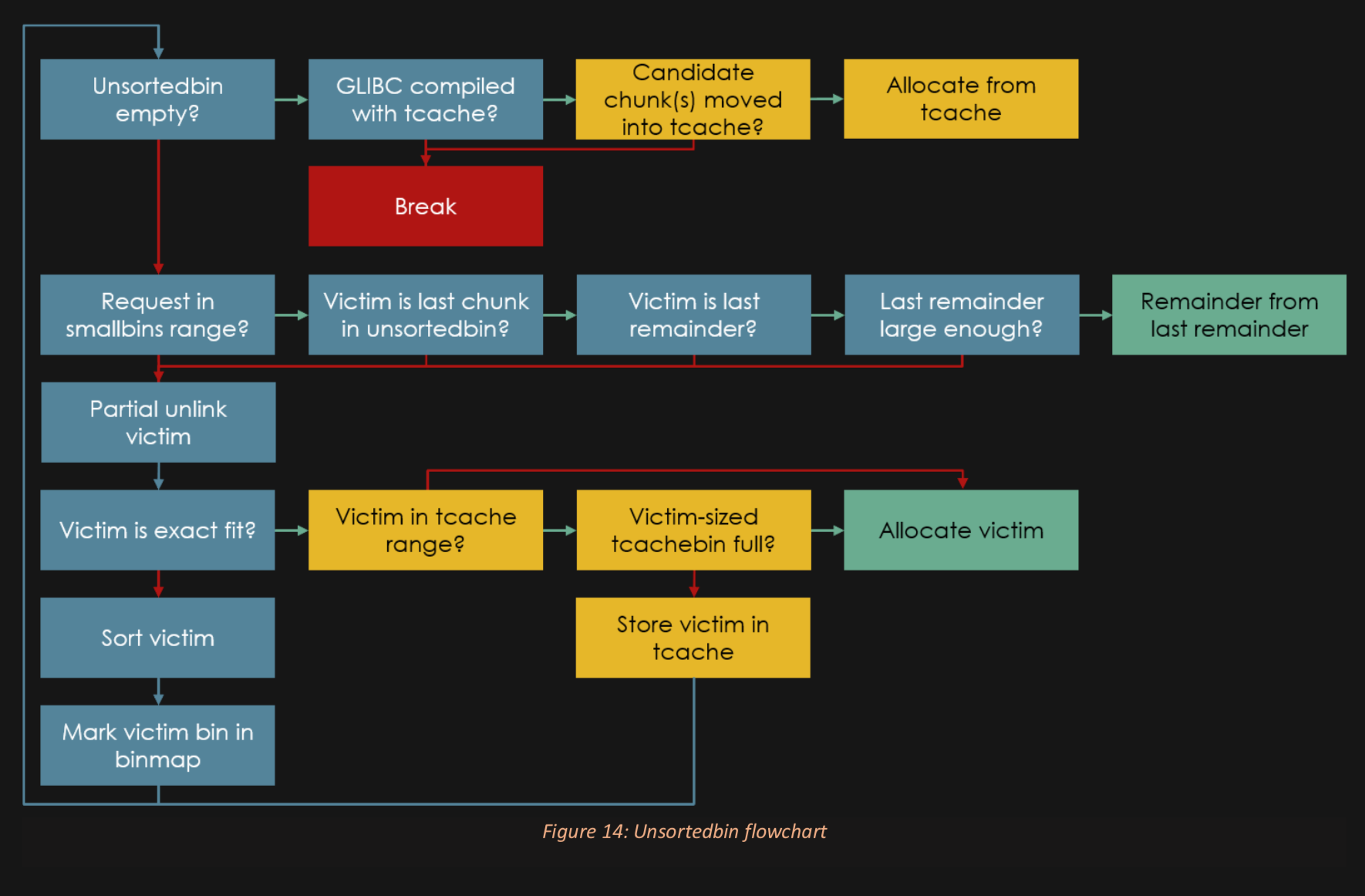
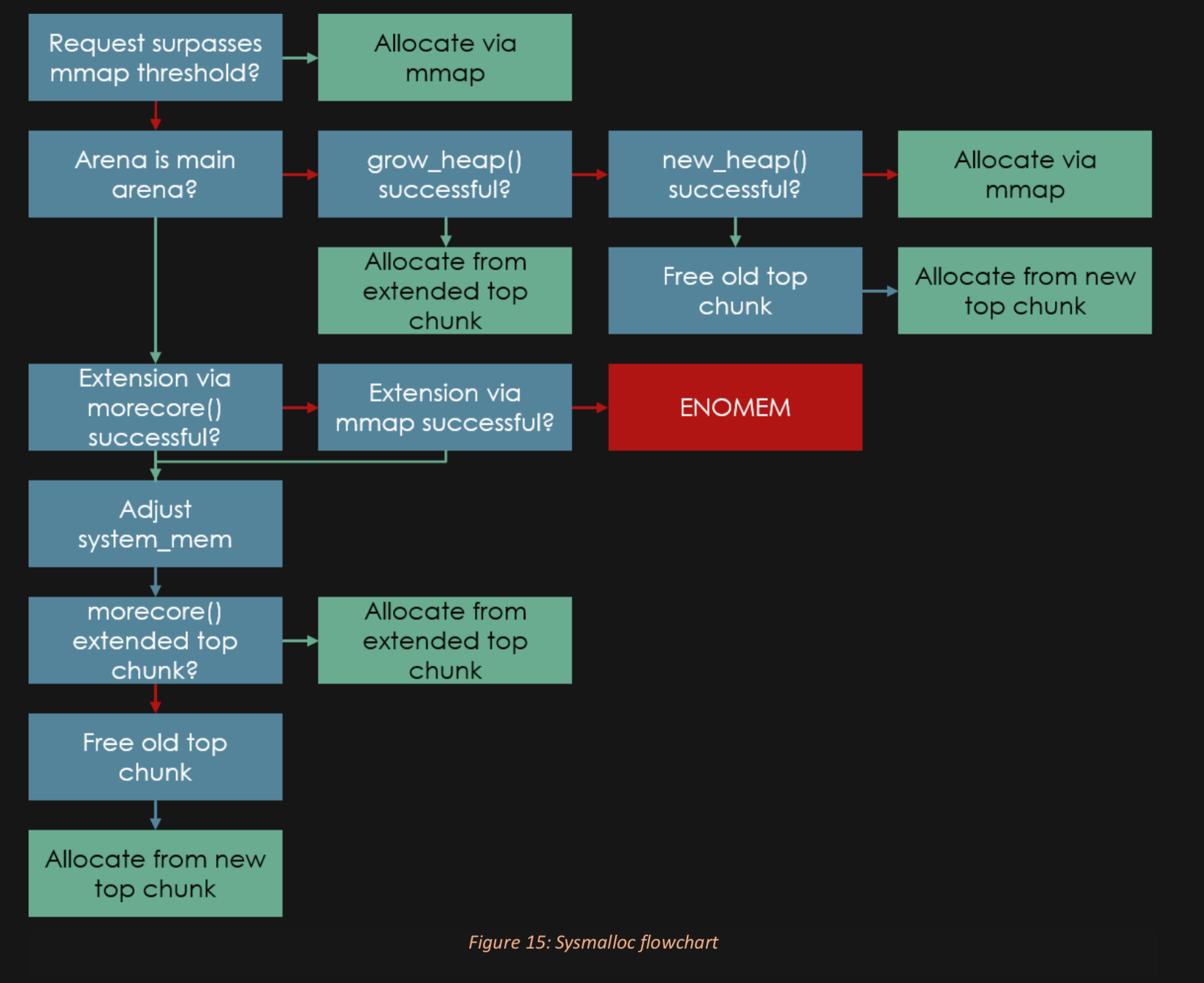
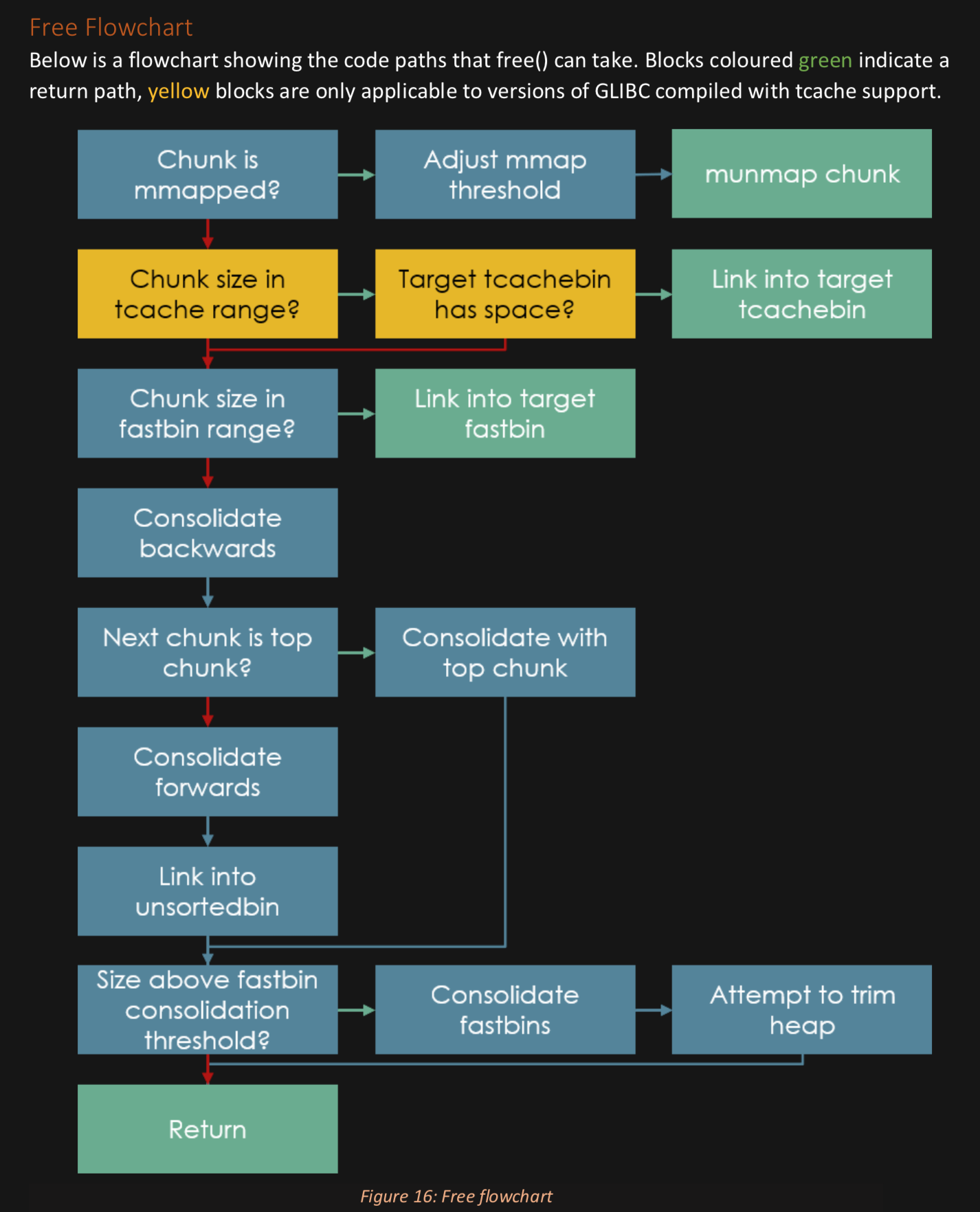
Don't like this style? Click here to change it! blue.css
Our compass through all of this is the desire for the following comfort food:
You're babies today and we're going to learn the warmth and love of the dining room table. So that as you venture into the wilderness you'll do your best to recreate this ritual in ever harsher environments.
It's "easy" just:
Of course, then you need to know a few lower level things.
For some carefully chosen size x
To understand why we'll need more intel.
This is a typical CTF style setup. Where we have this sort of smallest possible CRUD (Create, Read, Update, Destroy) setup.
Here is a sort of starter pwntools script for this kind of problem:
So let's try to get a leak on this program. The plan is to ask for space, free that space, view that space (this is the coder's vulnerability BTW).
Some stuff could go wrong.
Let's run this in gdb/pwndbg and look at the heap after the various mallocs and frees.
OK answering the questions.
malloc chunks, free chunks, view those free'd chunks.
Some possible reasons:
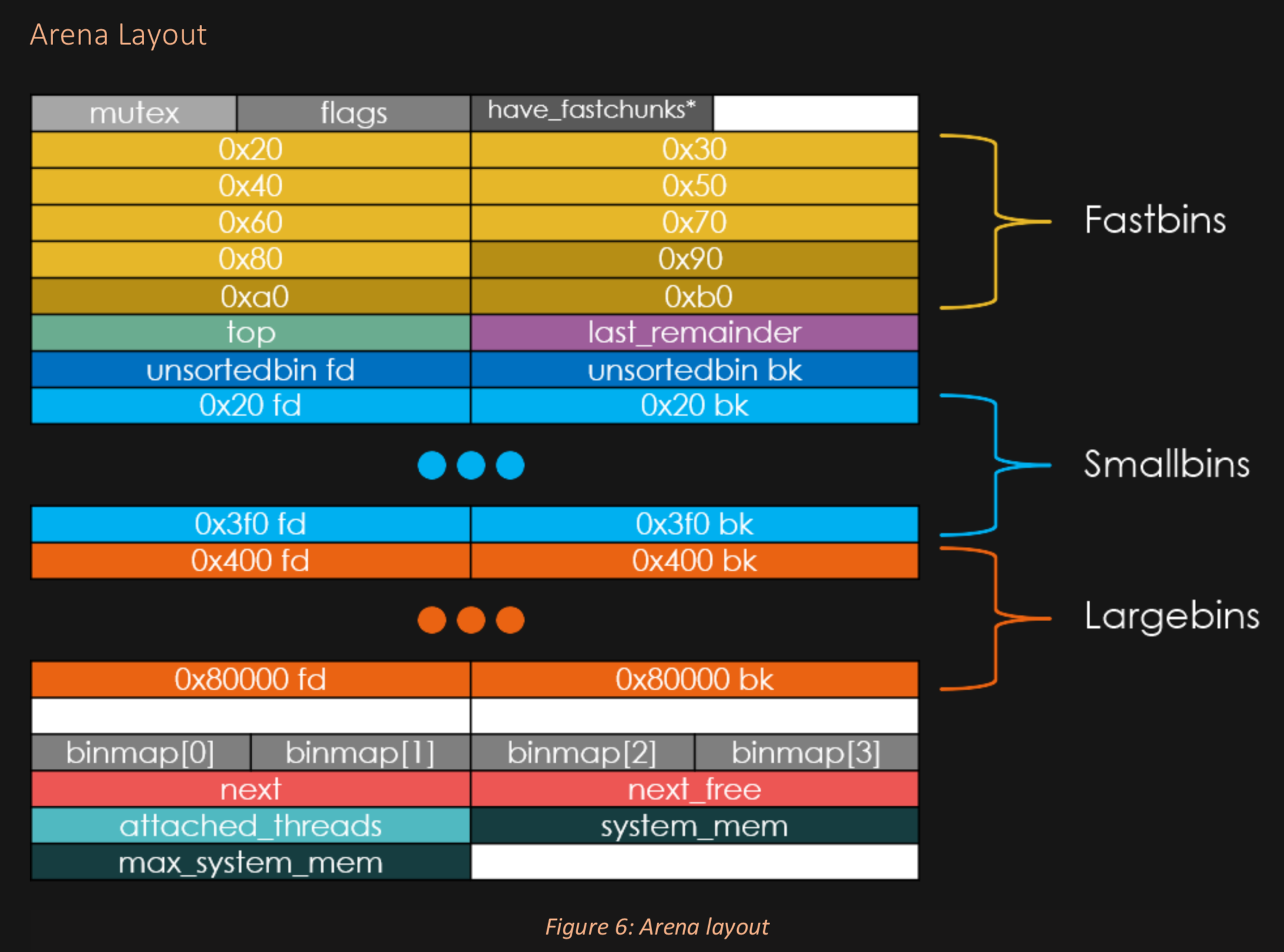
Mental models to explain those 3:
Well below are some useful guides.
ALSO it is nice to know the:
We should probably make a bookmark to learn how each of these 5 are used and why and various subtleties.
But let's just learn their names and fill in details as we go.
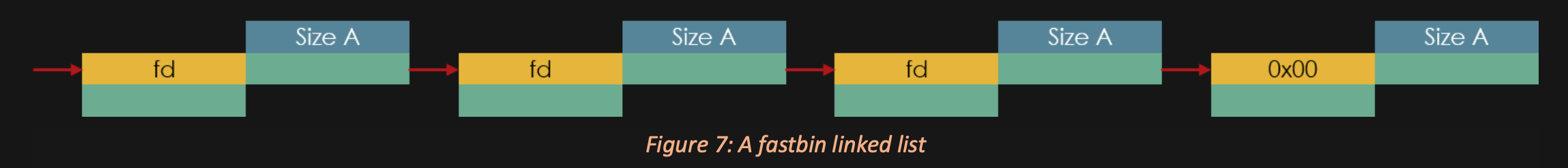
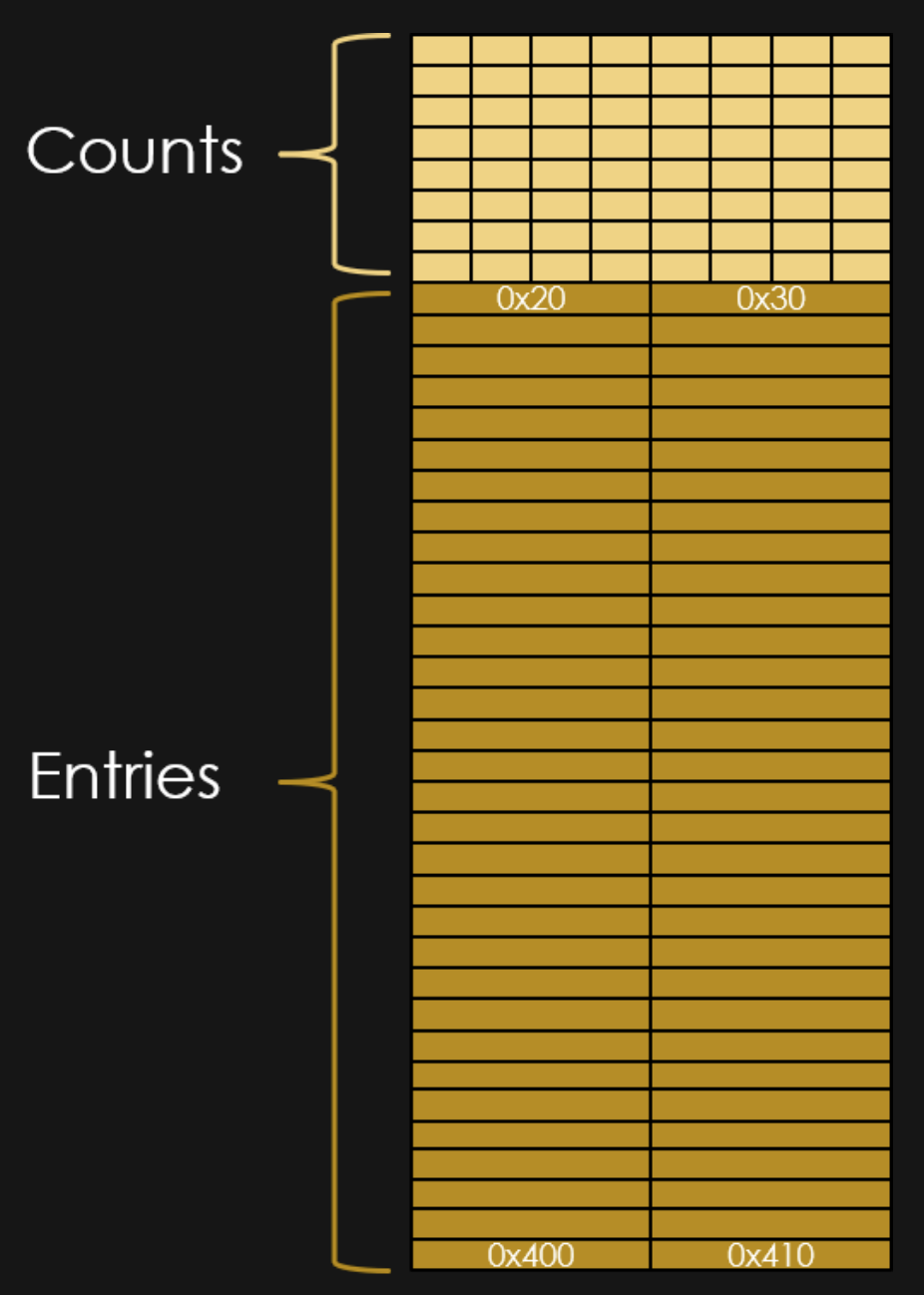
TCACHE puts the address of the previous "HEAD" into the chunk, but that address is ALWAYS in the heap segment.
FASTBINS act the same exact way.
The first UNSORTED BIN chunk links to GLIBC! Twice in fact!
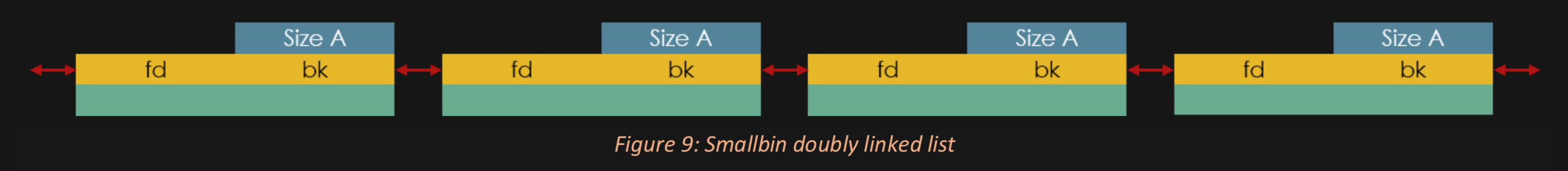
Later things added to the UNSORTED BIN will link to other chunks (it's doubly circularly linked and the head starts in glibc)
SMALL BINS are also linked to glibc and each other but a slightly different glibc address based on the size.
LARGE BINS are also linked to glibc and each other (and "fast-linked" to other size chunks) but a slightly different glibc address based on the size.
The easiest leaks might be all you need (if a heap leak is good enough). But if you need a glibc leak you'll need to know HOW to force a chunk into the unsorted bin.
If you need to get a bin into the SMALLBINS or into the LARGEBINS (Q6 will give you a why) then you'll need to know even more.
So if you are lucky you don't need to understand, and the more debugging you need to do the more you need to understand to do that well.
Sometimes, by bad luck, there is a null byte in your address. So when we print the leak the printf stops before giving you everything.
In that case you can try to move, intentionally into a DIFFERENT BIN so the address is just a little different.
If the null byte is in the randomized part of the address you can just run again and not be unlucky.









