Heap Reference Guides:
I'm gonna drop these here for reference in the notes later:
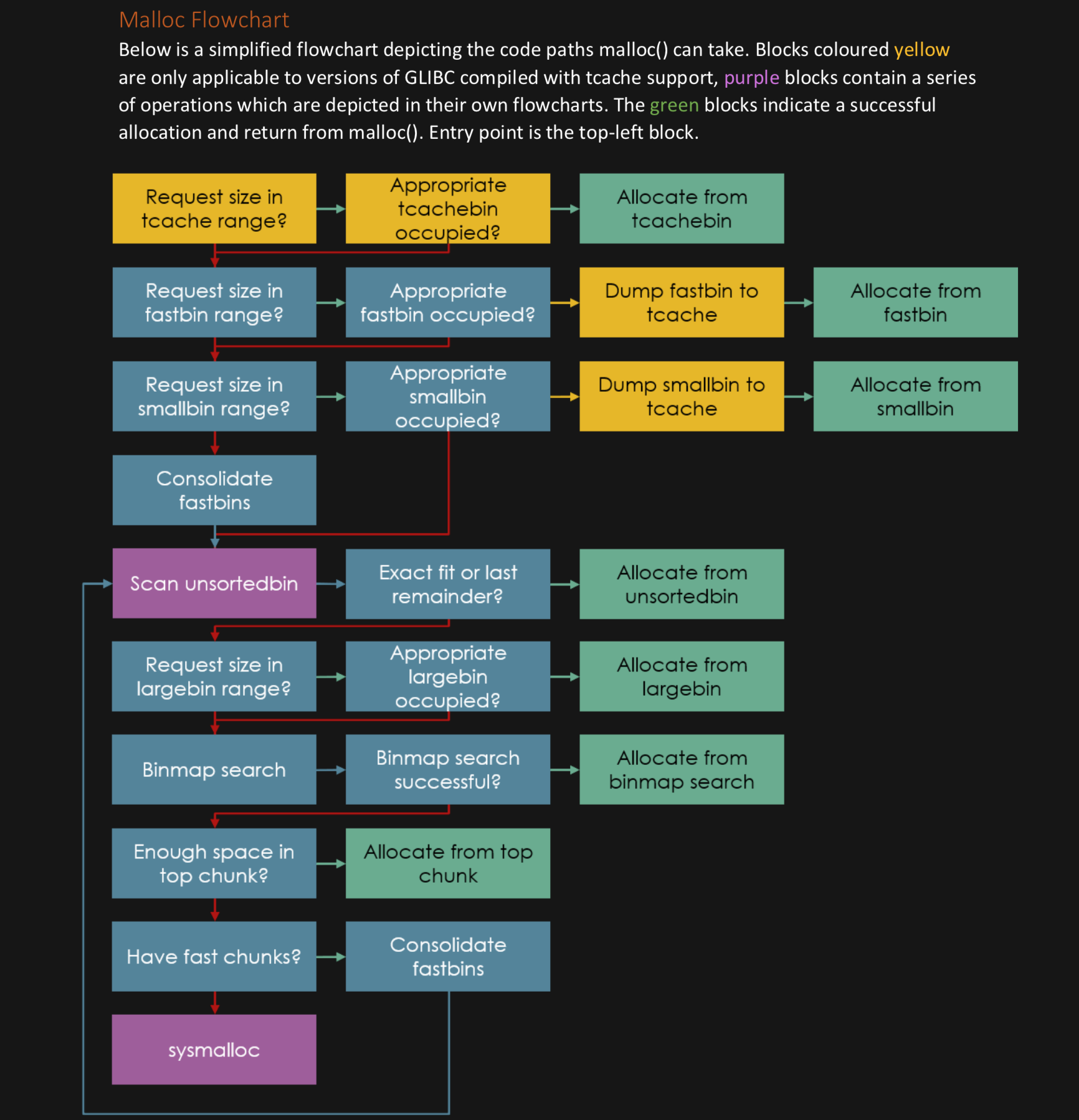
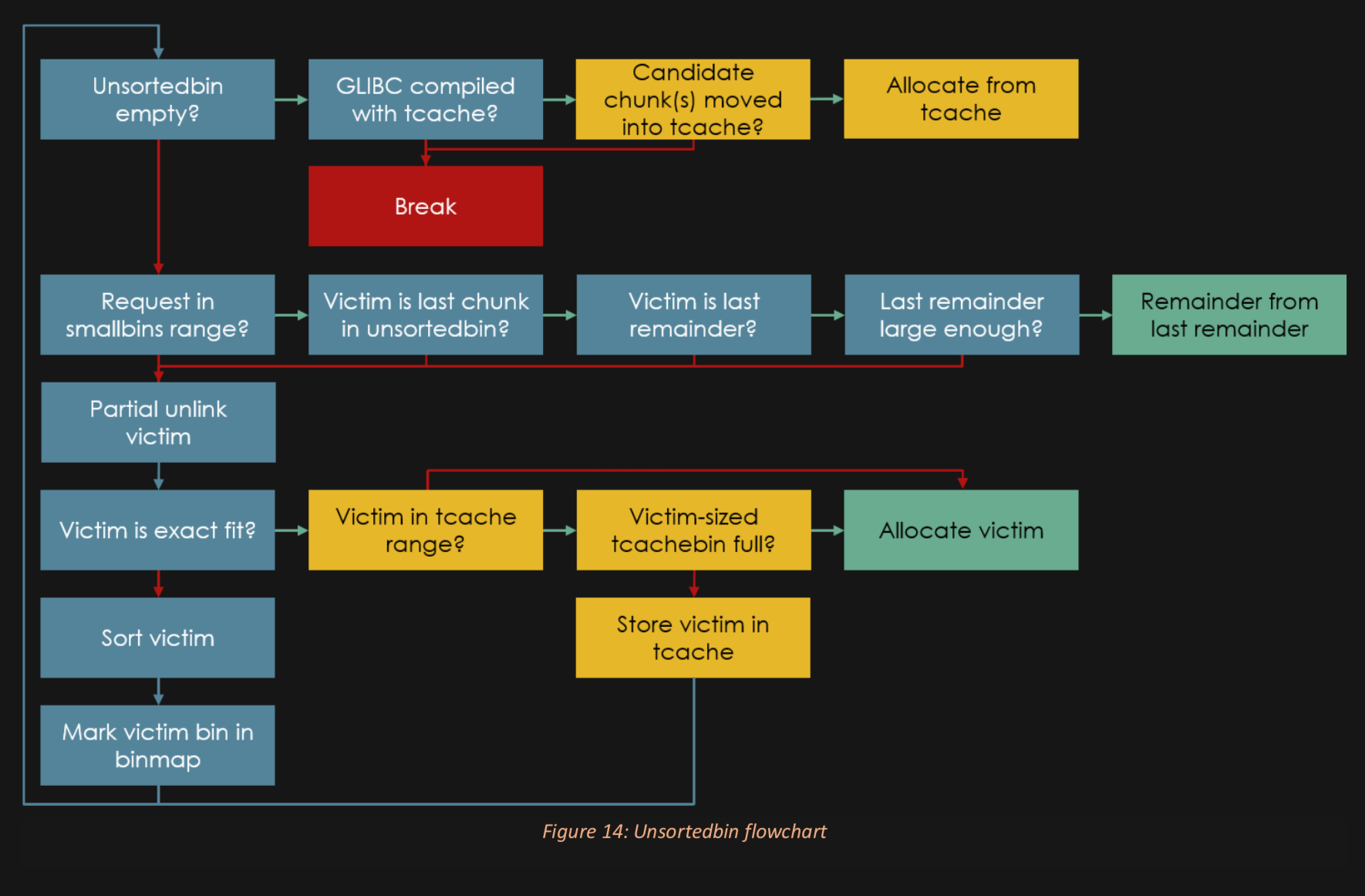
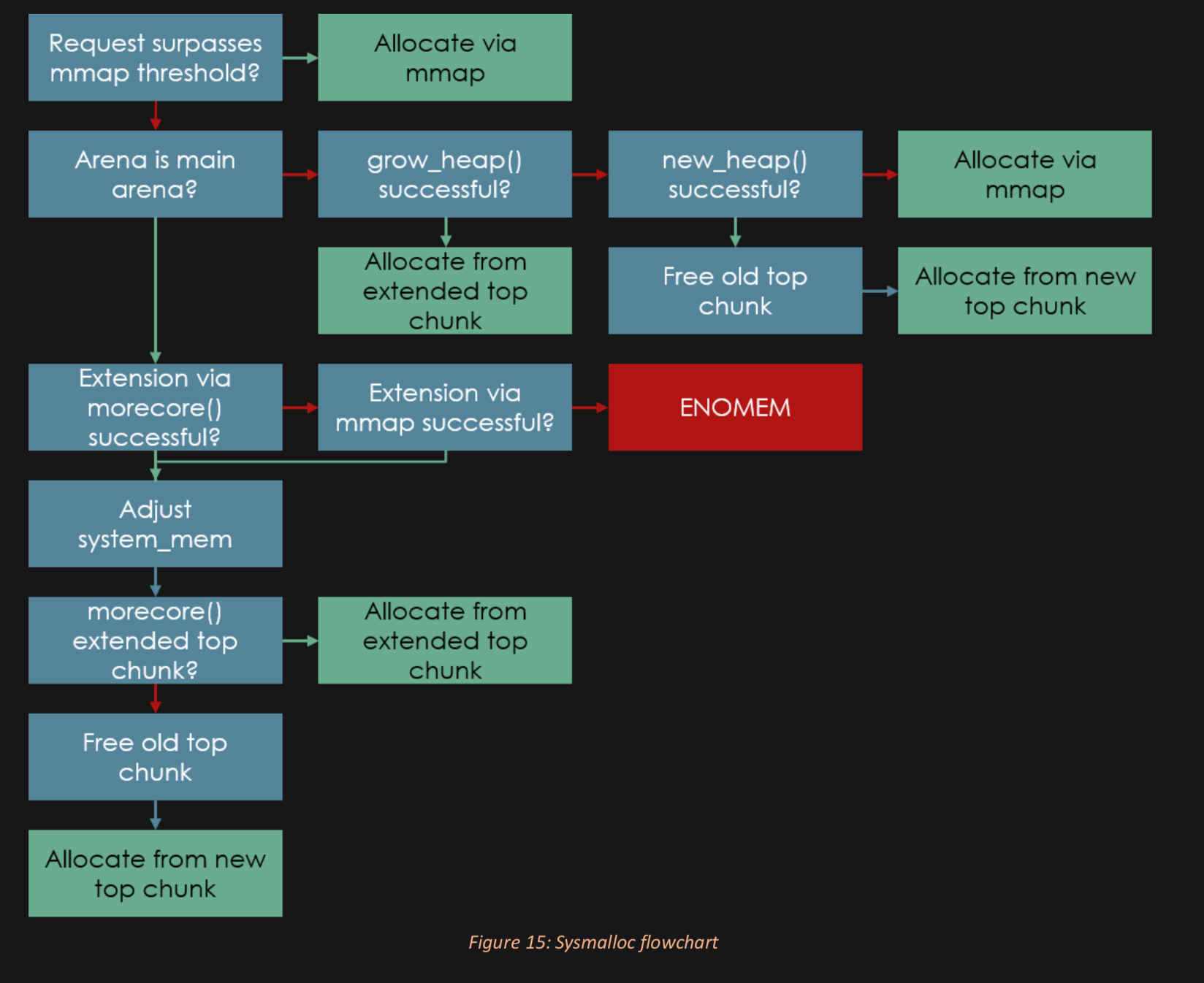
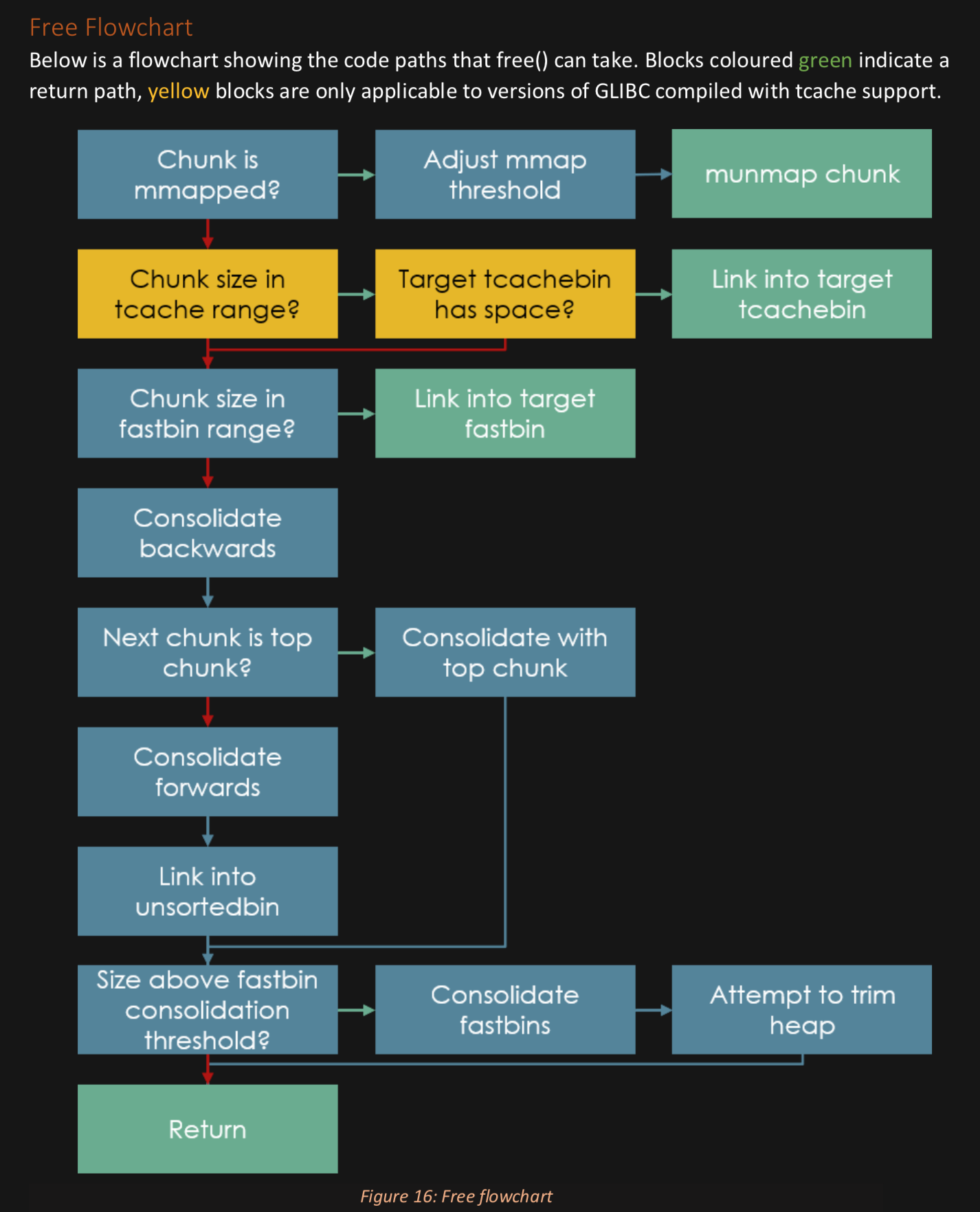
Don't like this style? Click here to change it! blue.css
Our compass through all of this is the desire for the following comfort food:
You're babies today and we're going to learn the warmth and love of the dining room table. So that as you venture into the wilderness you'll do your best to recreate this ritual in ever harsher environments.
It's "easy" just:
Of course, then you need to know a few lower level things.
This is a typical CTF style setup. Where we have this sort of smallest possible CRUD (Create, Read, Update, Destroy) setup.
Here is a sort of starter pwntools script for this kind of problem:
So let's try to get a leak on this program. The plan is to ask for space, free that space, view that space (this is the coder's vulnerability BTW).
Some stuff could go wrong.
Let's run this in gdb/pwndbg and look at the heap after the various mallocs and frees.
Mental models to explain those 3:
Well below are some useful guides.
ALSO it is nice to know the:
We should probably make a bookmark to learn how each of these 5 are used and why and various subtleties.
But let's just learn their names and fill in details as we go.
I'm gonna drop these here for reference in the notes later:



