Heap Reference Guides:
I'm gonna drop these here for reference in the notes later:
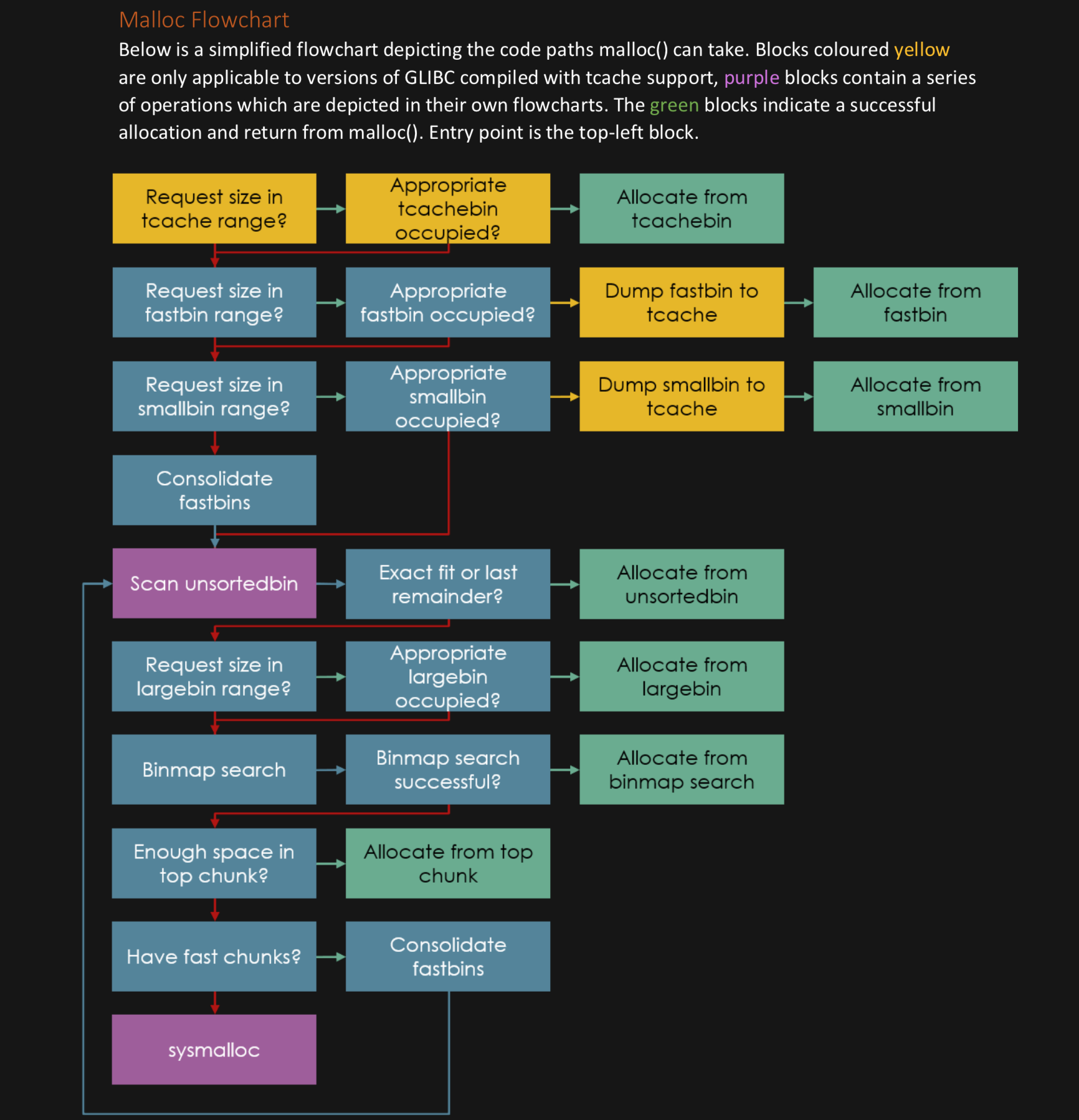
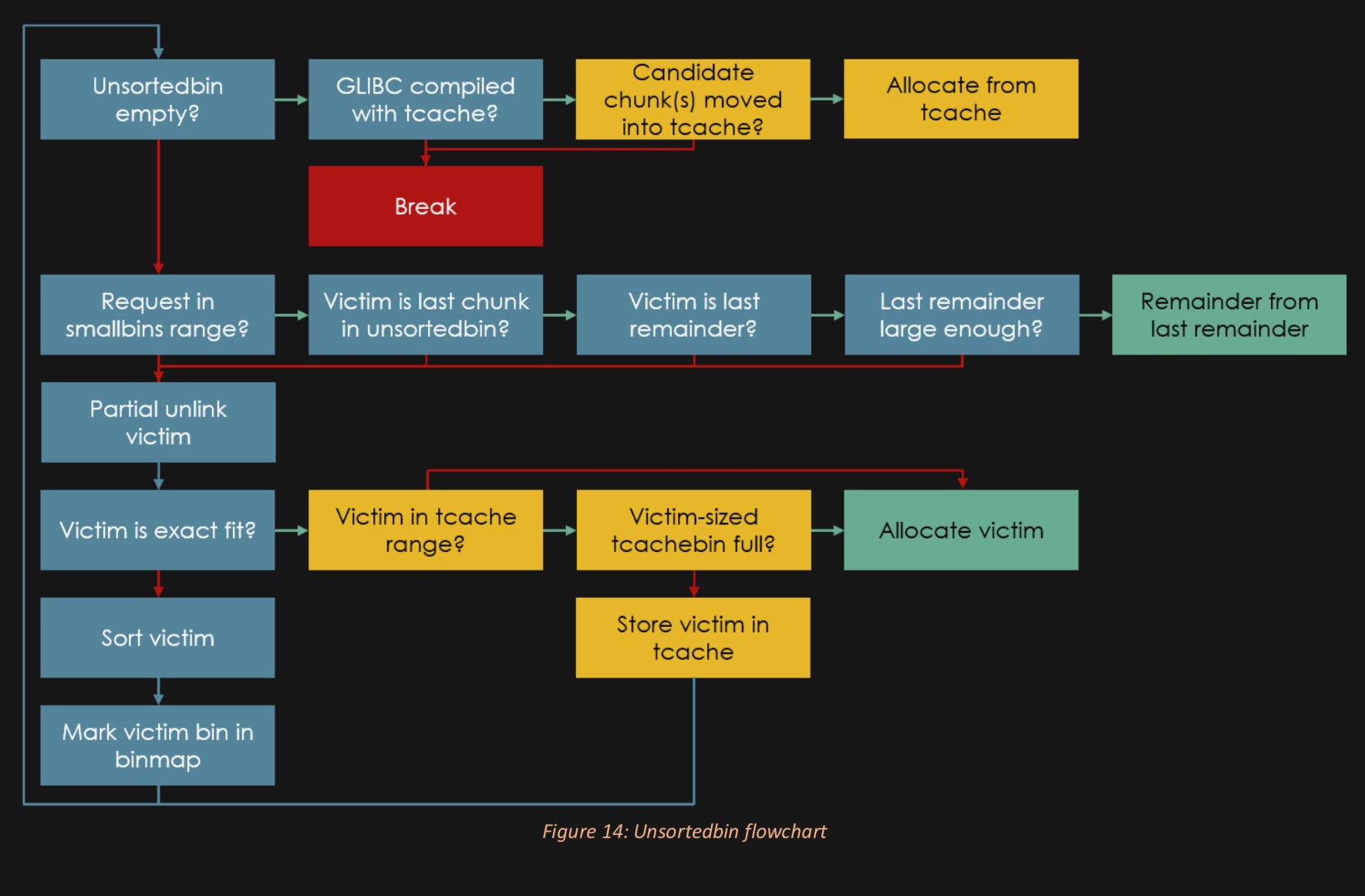
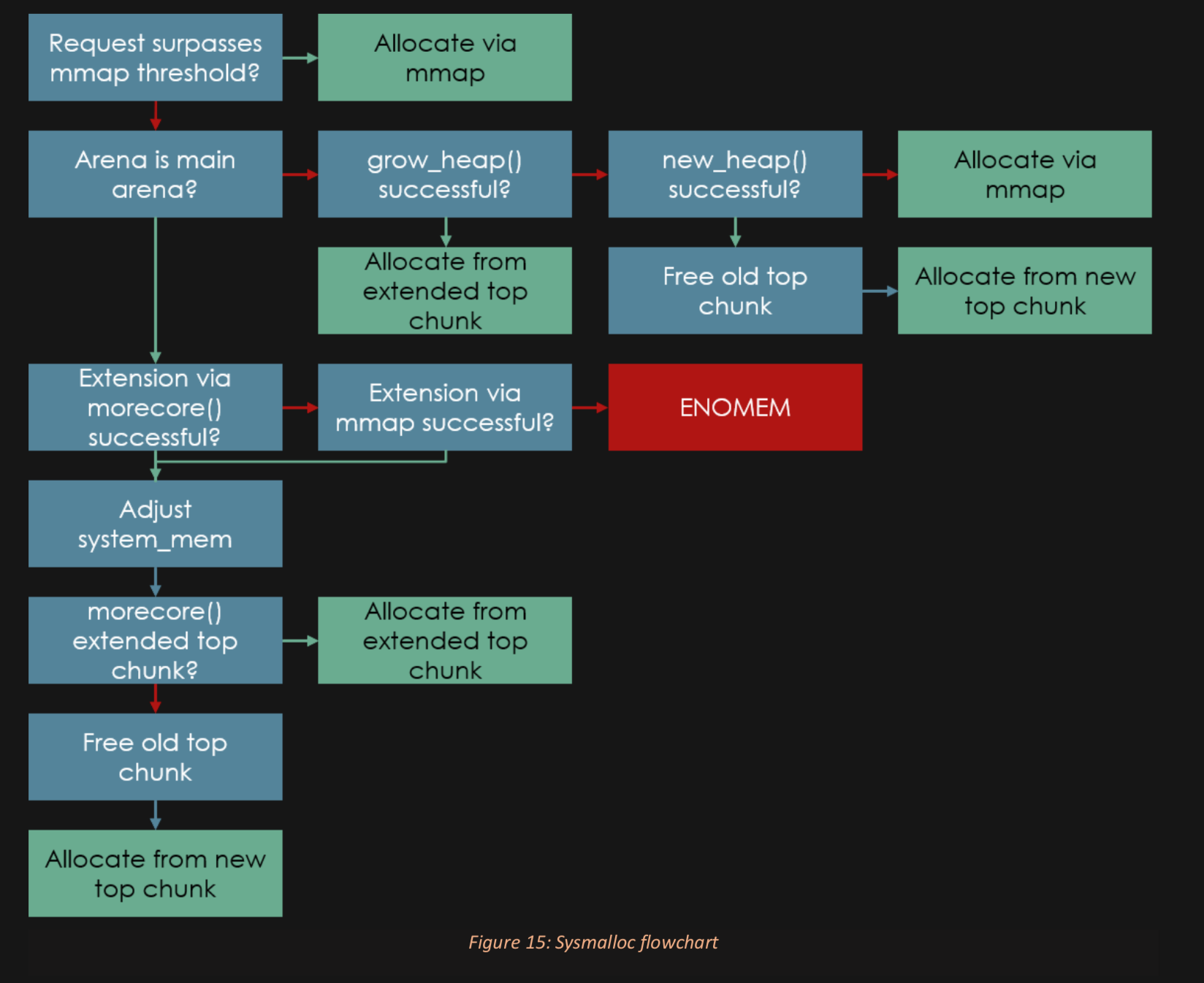
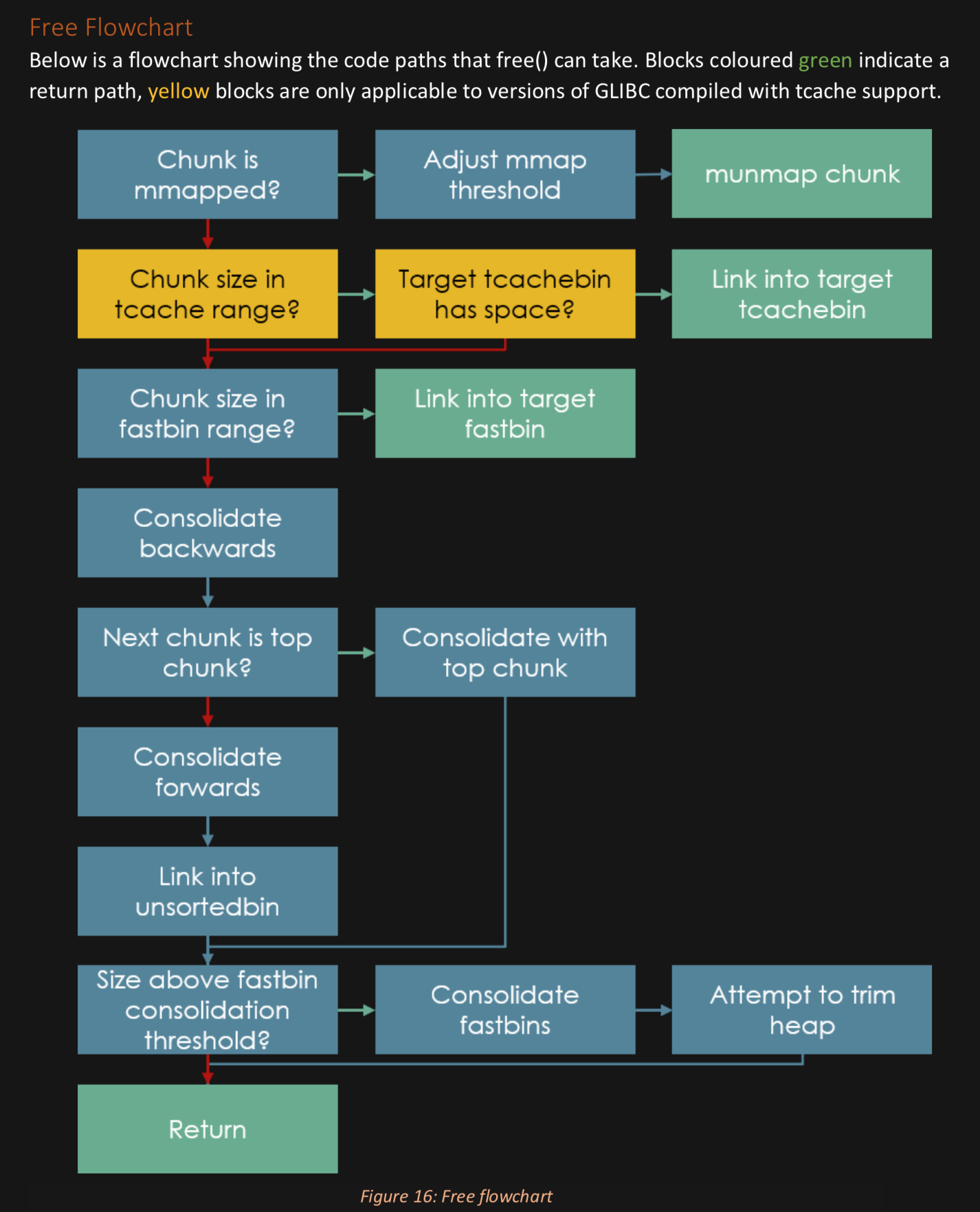
Don't like this style? Click here to change it! blue.css
Alright what are our goals?
malloc and freemain_arena?These are the same as they always been in a way, these 3 a part of all hacks.
So I'm going to teach you ONE MAJOR heap hack in pieces.
We will get to know this one which I'll call mom's spaghetti, you know, comfort food.
THEN once we know mom's spaghetti well we're going to face obstacles that prevent it.
We'll learn OTHER HACKS as bastardizations of Mom's Spaghetti.
I want to just do the hack I want... oh I can't? How about if I change one part? OK now I can hack again.
That's my guide to handling all of the uncertainty.
Here's a rough cut of mom's spaghetti, which won't make sense yet, but my job is now to get you learn mom's spaghetti, so I'll revisit this daily:
Our goal is to understand those three tricks inside and out. Once we're good at that we'll go into the variations.
https://github.com/pwndbg/pwndbg should be available in your pwndockers but in the other environments you'll need to install it.
OK let's just make a program to call malloc and free and see what happens.
Inspecting the heap with vis bins and heap. 1) Let's write a program, 2) Let's use gdb with pwndbg and 3) Let's start and step through.
Now let's look at a typical CTF style Heap setup:
This sort of state-machine menu is classic CTF exploit stuff, and is actually surprisingly easy to inspect/debug/work with.
I'm gonna drop these here for reference in the notes later:



